Chapter 1: Post-Internship
Spending 3 months in IT risk consulting was definitely super chill, sort of like a “retirement role” that I could see myself settling into later in life. But alas, I soon realized that this wasn’t the path I wanted to pursue, at least not while I was still a young and ambitious lobster with a deep passion for DFIR & Blue Team. I was locked in in securing a full-time position that had the job scope I was interested in. However, competition was fierce during that period. Every position required experience, how was I supposed to gain experience without first getting hired?

You Snooze, You Lose
A quick flashback on my 2023 self, I was just your typical clueless degree student, spending his days playing video games all day without doing anything cybersecurity-related. But that all changed when a classmate of mine dragged me into joining a local CTF, I was pretty much hooked into competing in CTFs ever since. The thrill of solving challenges while learning about something I was genuinely interested in? Yeah, that was enough to turn my gaming addiction into a CTF obsession.

Here’s the thing, my internship had little to no projects that I could work on since it was client-based. So, I spent my days grinding through multiple online CTFs, Hack The Box challenges and certifications to upskill before entering the job market. Why waste time doing nothing at home when I could be “gaming” with cybersecurity challenges, amirite?
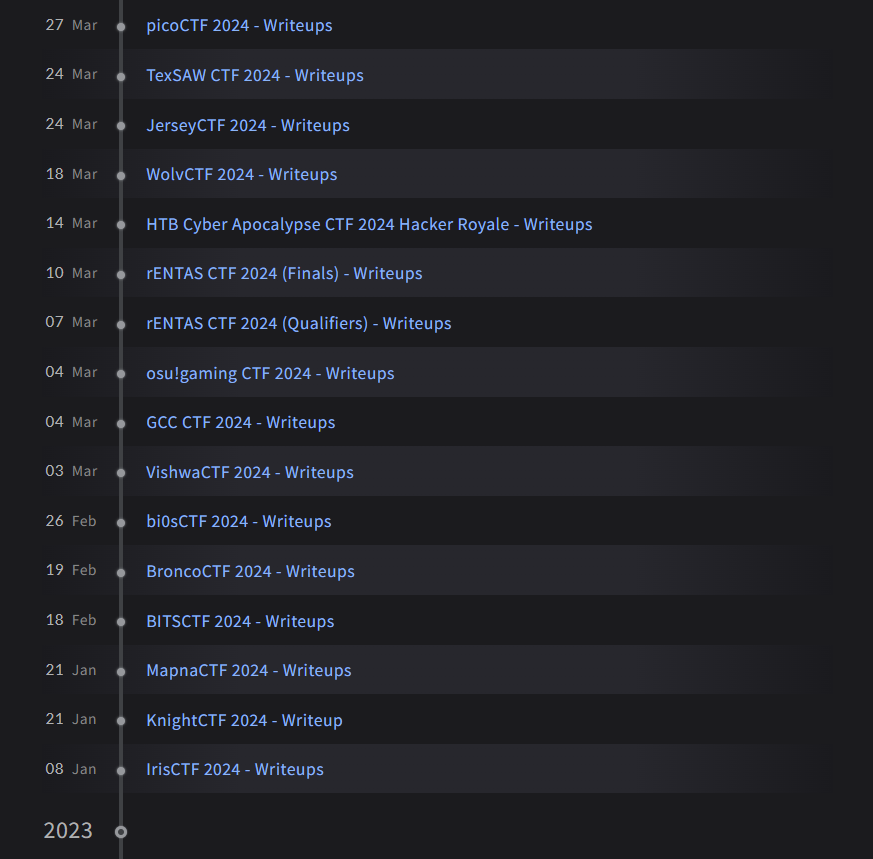
At the same time, I was finally convinced by the same classmate to actively attend local meetups to connect with professionals and gain firsthand insights into the realities of working in the field while yapping about how a certain local CTF was utterly bad during that month (iykyk).

The Reality of Job Hunting
Not gonna lie, my job hunt experience wasn’t as bad as what most fresh graduates or Redditors make it out to be. Maybe Lady Luck was on my side that month? Or maybe I was just too naive to realize I wasn’t setting the right expectations for what a decent job should be? Honestly, I could never tell. But I can assure you that I was getting more callbacks and offer letters compared to my internship days (What CTF grind does to a mf).
One thing I’ve noticed among many fresh graduates was focusing on getting high CGPA and expensive certifications, thinking that these would be the golden ticket to landing a job. Well, the reality is…it’s not as complex as you might think. Now, I’m not saying that landing a job overseas is easy, but in Malaysia? Anyone capable in showing their employer that they have the passion and attitude to learn and grow in the field can easily secure an entry-level position in a relatively small company to start out their cybersecurity career. Sprinkle in some networking, projects, CTFs and a bit of luck, boom, you have yourself a job. So what are you waiting for, go out and touch grass.
Subplot: The Sherlocks Guy
Just a quick funny story that I vividly remember. During the local meetup at SherpaSec, I was too nervous to approach any employers and “goats” since I was still a nobody in the local scene. Instead, I stuck with people I know from other universities and had a blast meeting them in person. As the meetup wrapped up, I was introduced to a chill employer who looked oddly familiar. Oh right, I had just connected with him on LinkedIn a few days earlier after coming across his comments on several cybersecurity posts. Before I could even introduce myself, he recognized me instantly:
Oh, you’re the Hack The Box Sherlocks guy!
Remember the grindfest I put myself through over the past few months? Turns out, I was pretty much known to be the only person there who actively solved and posted about Hack The Box Sherlocks challenges on LinkedIn. After a quick chat about why I was playing it in the first place and how these challenges shaped my skills, he immediately offered me a chance to work under him, asking me to send over my CV via LinkedIn for further discussions. PS: I didn’t accept his job offer, but it was a great experience meeting up with him.
Chapter 2: The Journey Begins
Ok enough yapping about the past. Fast forwarding to June 2024, I accepted a job offer from a U.S. fintech company and officially started my full-time role as a cybersecurity analyst. Walking into the office on my first day, I was pretty excited since I could finally have the opportunity to work with a SIEM in a real production environment and collaborate with experienced professionals in the cybersecurity field. However, that excitement was short-lived. Before long, I found myself struggling with huge imposter syndrome and feelings of self-doubt, which began to take a toll on me heavily.
The Quiet Struggle
During my first few weeks, my team lead gave me a quick rundown on the team structure, workflows and several onboarding tasks since he was going to take a few days off for his vacation. During that period, I was pretty much supervised by my senior colleague instead. One day while I was going through the onboarding tasks, my senior colleague assigned me to investigate an incident related to a traffic spike in our mobile traffic. Obviously, I was still new so I had no idea how the SIEM works (it was not a common SIEM like Splunk or ELK stack) and was unfamiliar with the company infrastructure. Due to these struggles, I had a hard time investigating the incident and had to constantly request help from my senior, only to be met with even more questions from him that I could not answer.
With hindsight, the problems I faced were indeed dumb and would’ve been easy to figure out if I had just read the documentation properly. I also have to admit that the senior colleague was most likely just trying to guide me towards the answer without giving it to me directly. Maybe because they were expecting more from me due to my CTF background? Or maybe I was just arrogant and expected some handholding for my first few weeks at work? Well, at that point it was too late, Imposter Syndrome (the devil of cybersecurity) has hit me hard and I felt pretty shitty for the whole month.
Speak No Evil
Since then, I continued to struggle in triaging simple alerts since I was nervous to ask more questions to my senior colleagues. Again, dumb move on my part. Please reach out to someone if you are struggling, no matter the question. I’ve also pretty much lost all my confidence and self-esteem, causing me to be socially awkward during lunch breaks and team building sessions. I was pretty much looking at my phone constantly, being socially inept throughout the day. This caused difficulties in building chemistry between me and my team and everyday was pretty much a awkward situation for me.
Just a quick sidetrack, if you were a close friend of mine, you would know that I am pretty much a full-time yapper and shitposter that can talk about anything under the sun, especially online. But when it comes to work, I was really having difficulties in finding a topic that would click with my senior colleagues. The more I think about this, the more I realized that age gap plays a huge role in this. Here is an amazing tweet that was made by Fareed, a person I look up to heavily: https://x.com/warlocksmurf/status/1898047730406343006
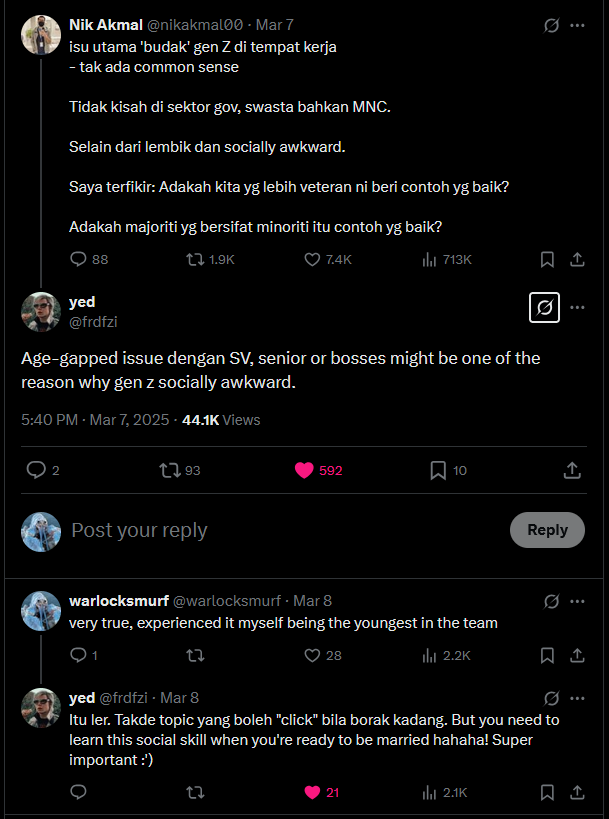
To translate and quote both of his tweets:
The age-gapped issue with supervisors, seniors or bosses might be one of the reason why GenZ are socially awkward.
This. There are not topics that will “click” when chatting sometimes. But you need to learn this social skill when you’re ready to be married hahaha! Super important :’)
Not gonna lie, these tweets just made me respect Fareed as a person even more. The fact that he recognizes the struggles juniors face when communicating with seniors due to the age gap is reassuring.
Is It Worth It?
After my team lead came back from his vacation, he assigned me with several threat hunts, phishing investigations and Cloudflare tasks which I did fairly well. Realizing my hope of passing my job probation was returning, was yet again crushed when I struggled to do a simple task that required intermediate knowledge in Terraform and AWS. At that moment, my mind was pretty much blank and I was just staring at the screen, wondering…
What the hell is Terraform and how the f@#k do I use GitHub CLI
Yet again, I was too afraid to ask my seniors about this so I reached out to a close-friend of mine who works in the SRE department for questions on setting up Terraform. Each day passes where I was assigned with a task and had slight struggles with each of them, to the point where I was on the verge of rage quitting it all.

Walking back home from the MRT, overwhelmed by doubts and wondering to myself, was it worth it? Constantly thinking to myself that maybe I am not suited to be a cybersecurity analyst after all and I should just resign after my probation ends, the sudden fear of losing it all due to my lack of self-confidence and social skills to at least commununicate with my team lead about the struggles I have with this.
Lying on my bed tired and depressed, thinking to myself:
“Is it worth it to stay? Should I just leave after 3 months? Do I feel like a member of a team at all?”
These questions have always been in my mind and it was a struggle to even find an answer to them. Before I could even answer these questions, something happened in the team that changed my perspective entirely.
Chapter 3: The Downfall
Waking up from my daily slumber, I came into the security room and was conducting my daily security operation duties while waiting for the rest of the team to arrive. During our weekly meeting, my team lead officially annouced about his resignation and will be putting me to be supervised by the head of cybersecurity (who is also a person I knew from SherpaSec). Funnily enough, the resignation might have been the catalyst for the team’s downfall in the future.

Skipping a few months ahead until the end of Q3’24, I was praised for my efforts after presenting my research on improving our threat detection using JA4 hashes. I was also given praise on my reverse engineering skills when I made an in-depth writeup on a famous macOS malware that was flagged by our EDR (you can read more about it here). These small appreciations gave me a quick dopamine and confidence boost, but it was short-lived. A sudden annoucement was yet again made during our weekly meeting. This time, the head of cybersecurity and a colleague of mine (who is also my university classmate) officially announced about their resignation. Due to this change, I was once again supervised by a different person, this time the team lead of AppSec.
At that point, it really felt like a comedy skit. Have you ever witness a fresh graduate being assigned 3 different supervisors in just a span of 6 months, yeah it’s pretty rare lmao…

As time passes, each senior gradually resigned one after another. In a blink of an eye, I was pretty much alone in the security room, wondering when the next incident will occur and make me have the worse day of my life. I have to admit though, I do miss having them around in the security room despite not knowing them too well. They were the ones who actually guided me through my struggles and helped me grow despite my dumb struggles in the early days. But it is what it is.

Finale: A New Beginning
It’s 2025, I just had my salary increment and bonus from working multiple incident response shifts during Project Bengal that happened in December 2024. On top of that, HR finally managed to hire several new members to join the team. So, I was supposedly a “senior” in the team now and was tasked to guide the new members. It was pretty difficult to adapt to a new environment, but I managed to get along with the new members and was able to communicate with them effectively.
Also, a friend of mine from the CTF scene recently joined the AppSec team and he had strong experience in web application security. Hence, I could finally facilitate the return of purple team exercises in the team to identify vulnerabilities in our infrastructure. It was a great experience working with him and I’m looking forward to working with him in the future.
New Role, Same Old Lobster
Since the team was pretty much complete now, I decided to pivot to threat intelligience since I was super burntout from incident response and our team needed someone to rebuild the CTI workflow from scratch after “The Downfall”. I also wanted to learn about threat intelligience and how I can automate certain programs to study and research on a specific threat. Working as a threat intelligience analyst will be a daunting task this year, but it will definitely be worth it. Cheers to another great year!
Subplot: Uncovering My First Data Leak
Sometime around March, I was exploring Intel471 when I came across sensitive user credentials being traded on an underground marketplace, specifically Telegram. Downloading the credentials list, I thought it might be fake due to the weird usernames and password utilised by our users. However, after testing some of them on our login page, it managed to work and I was faced with the 2FA challenge.
At this point, I realized this could be a serious data leak, but I was still new in CTI and didn’t feel confident enough to bring it up. Despite the doubts, I created a Jira ticket to the fraud team for further analysis, detailing what I found and flagging it as a potential data leak. After a few days, the fraud team confirmed that the data were real and they were able to block some of the accounts. That moment marked the beginning of my journey in threat intelligence, and it taught me just how important it is to act fast, even when doubts creep in.
Subplot: Company Acquisition Turned to Opportunity?
Coincidentally, my company was acquired by a cybersecurity firm around the month of May. As someone interested in the field, I was genuinely excited to see how this acquisition would influence our team and the projects we were working on. It brought fresh opportunities for collaboration and knowledge sharing—much needed after several months of uncertainty. Interestingly, this acquisition also made me reconsider my plans to switch jobs. Instead of leaving this month, I decided to stay through the end of the year to experience the transition and hopefully learn a thing or two from the security researchers at the new company.
Don’t Be a Dumb Lobster
Ok finally the yapping is over. So what did I learn so far?
Don’t be afraid to ask questions, even if they sound dumb.
Lobsters are known for their hard shells, but they also have soft insides. Don’t be afraid to show your vulnerabilities and ask for help when you need it than to stay silent and struggle. That’s how we grow and become better at what we do. Remember, no one expects you to know everything from day one.
Imposter Syndrome is never-ending
Imposter syndrome is a real thing, but it doesn’t define who you are or what you’re capable of. It’s important to communicate openly and honestly with your team, even if it means admitting that you’re struggling.
Don’t be afraid to try something new
I have to admit, pivoting to threat intelligence was something I did not expect to do when I first started out. But again, the best growth happens when you step outside your comfort zone. It’s easy to stick to what you know, but the real magic lies in embracing the unknown. Every challenge, every mistake, and every success along the way teaches you something new.